Request attributes
Dynatrace tracks all requests, from end to end, and automatically monitors the services that underlie each transaction. The performance and attributes of each request can be analyzed in detail. You're not limited to just certain predefined attributes. You can also configure custom request attributes that you can use to improve filtering and analysis of web requests.
Request attributes are essentially key/value pairs that are associated with a particular service request. For example, if you have a travel website that tracks the destinations of each of your customers’ bookings, you can set up a destination attribute for each service request. The specific value of the destination attribute of each request is populated for you automatically on all calls that include a destination attribute (see the destination attribute example below). A single request might have multiple request attributes.
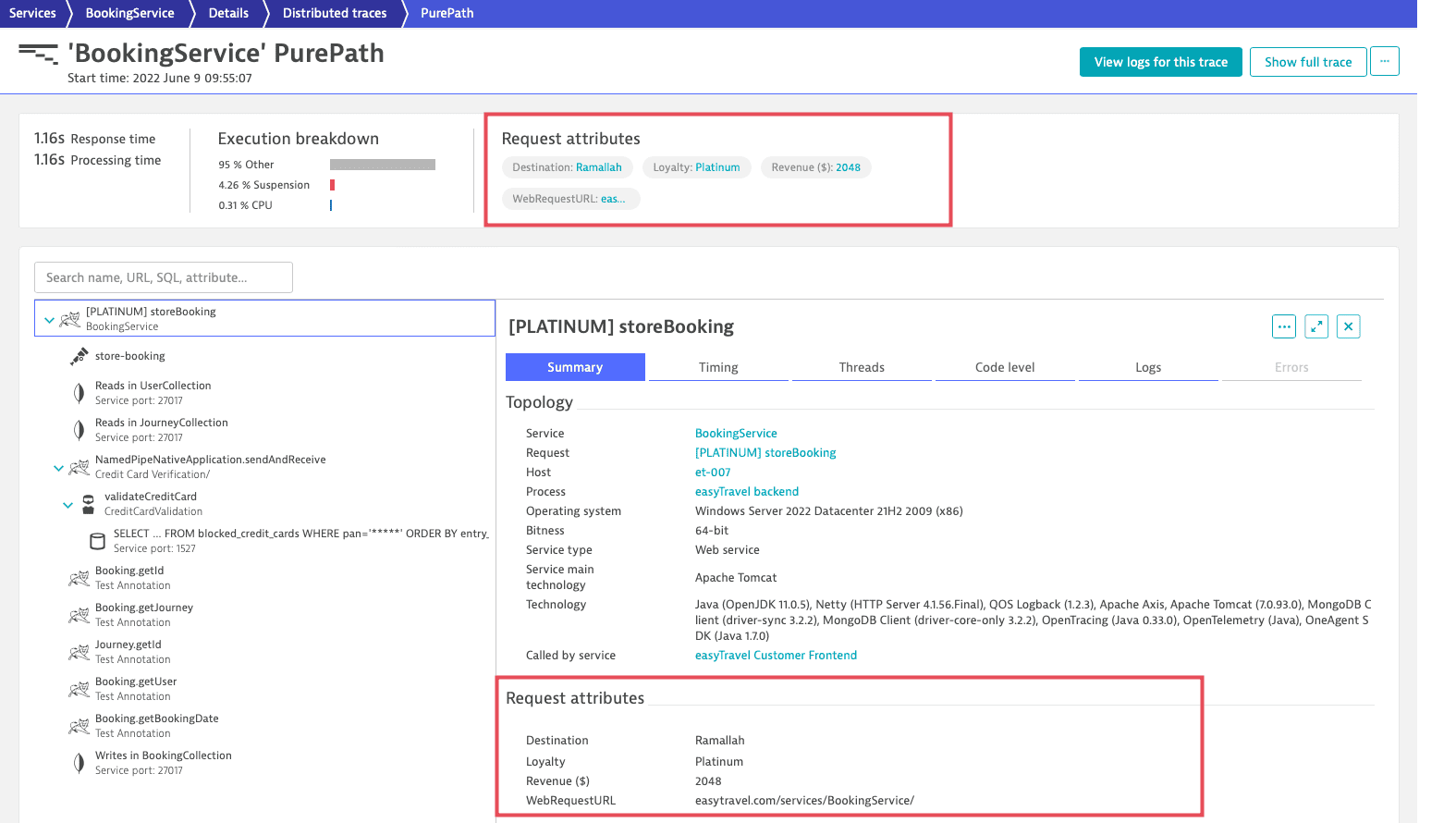
Multiple requests within a single distributed trace might have the same attribute but with different values.
Define request attributes
You can capture request attributes based on:
- Web request data
- Java, .NET, and PHP method arguments
- Any data captured with the OneAgent SDK
Confidential request attributes
As request attributes may include confidential values, Dynatrace makes it possible to mark a request attribute as confidential. To do this
- Go to Settings > Server-side service monitoring > Request attributes.
- Select Edit for the relevant request attribute.
- Select Request attribute contains confidential data.
With this setting enabled, Dynatrace users who don't have access to confidential data see only an obscured view of masked data. For example, while they can see all performance metrics related to the execution of a certain SQL statement, all sensitive values in the statement are represented with asterisks (*****), and so are hidden from unauthorized access.
How to make use of request attributes
Here are some examples of how you can use request attributes:
- Filter your monitoring data
- Define web-request naming rules
- Set up detection of business-logic related errors
- Enrich distributed traces analysis by adding metadata to distributed traces
- Create calculated metrics
- Create custom queries, segmentation, and aggregation of session data with User Session Query Language