Modern software systems face constant security threats. While integrating security measures throughout the software development lifecycle (SDLC) helps reduce risks, some vulnerabilities may still go undetected. Combining SDLC best practices with runtime validation helps organizations detect and remediate risks in production environments, ensuring robust, actionable protection while reducing noise and saving teams time by focusing only on the issues that matter most.
Recognize the unavoidable need for runtime security
No security strategy can guarantee absolute protection. Modern software complexity and dynamic threats mean some risks will evade detection (Figure 1). According to Dynatrace analysis, a significant portion of Fortune 500 companies remain vulnerable to known vulnerabilities, such as Spring4Shell.
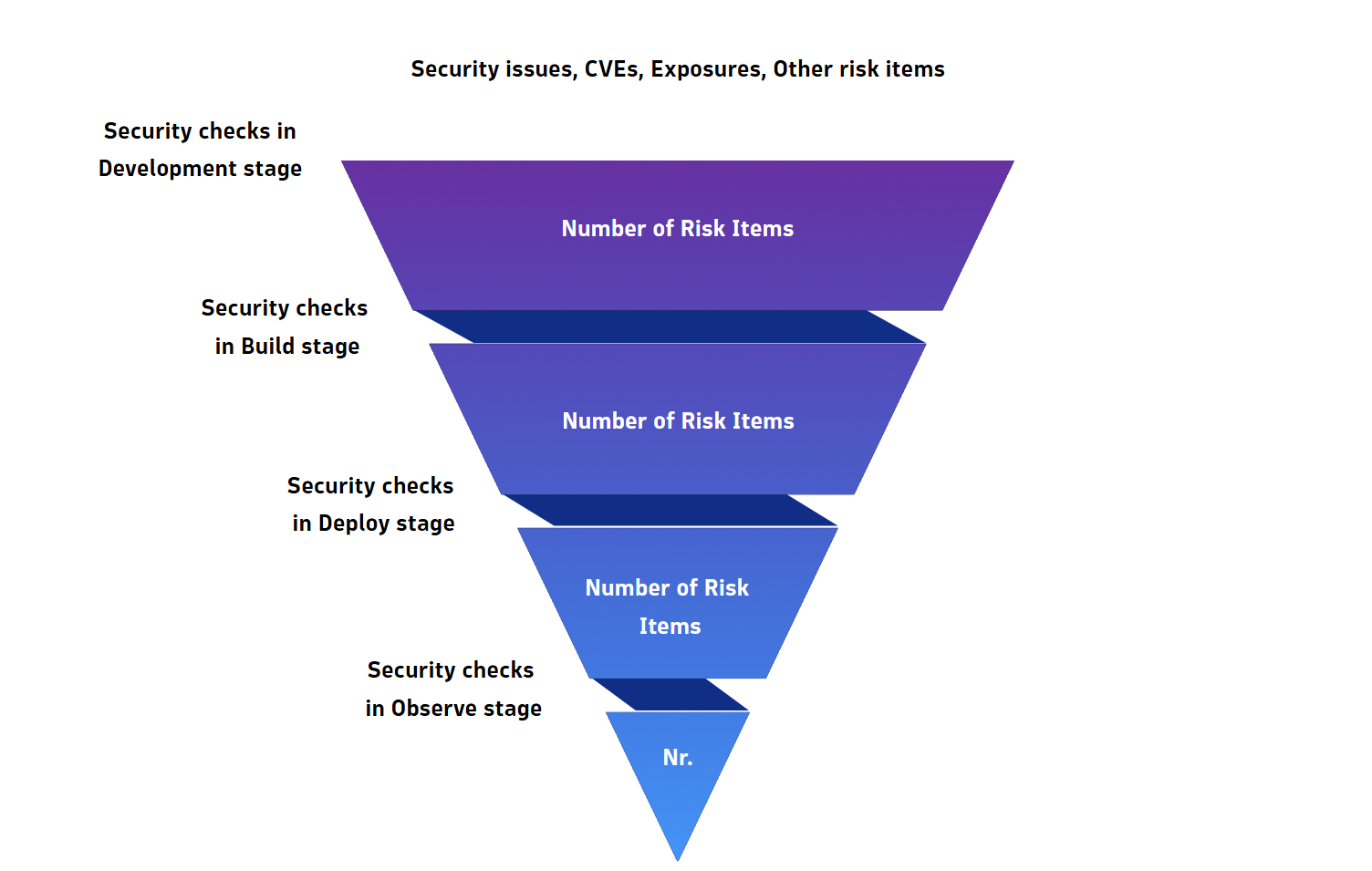
Left-shifted tools often lack runtime context, making it hard to prioritize vulnerabilities by real-world impact. Runtime security bridges this gap by continuously monitoring production environments, detecting and mitigating threats in real time. This approach helps organizations adapt to emerging risks instead of relying on pre-deployment checks.
Dynatrace addresses this challenge by adding runtime context to left-shifted security findings, enabling environment-aware vulnerability prioritization. Dynatrace Application Security integrates seamlessly with third-party tools to ingest and enrich vulnerability data with runtime context. This context-rich prioritization reduces cognitive overload for teams across the SDLC.
The value of defense-in-depth in SDLC
A defense-in-depth approach layers multiple security controls across the SDLC to build resilient applications that can withstand sophisticated attacks. Rather than relying on a single security measure, defense-in-depth supports the strategy that if one layer misses a vulnerability, another will catch it.
This approach gains added relevance as modern development practices accelerate release cycles, often introducing new risks at every stage. By embedding security from the earliest phases of development through to production monitoring, teams can proactively identify, mitigate, and respond to threats before they escalate. Figure 2 illustrates this multi-layered approach, mapping out key capabilities across four critical SDLC phases: Development, Build, Deploy, and Observe (encompassing the commonly referred-to phases of runtime and monitoring).
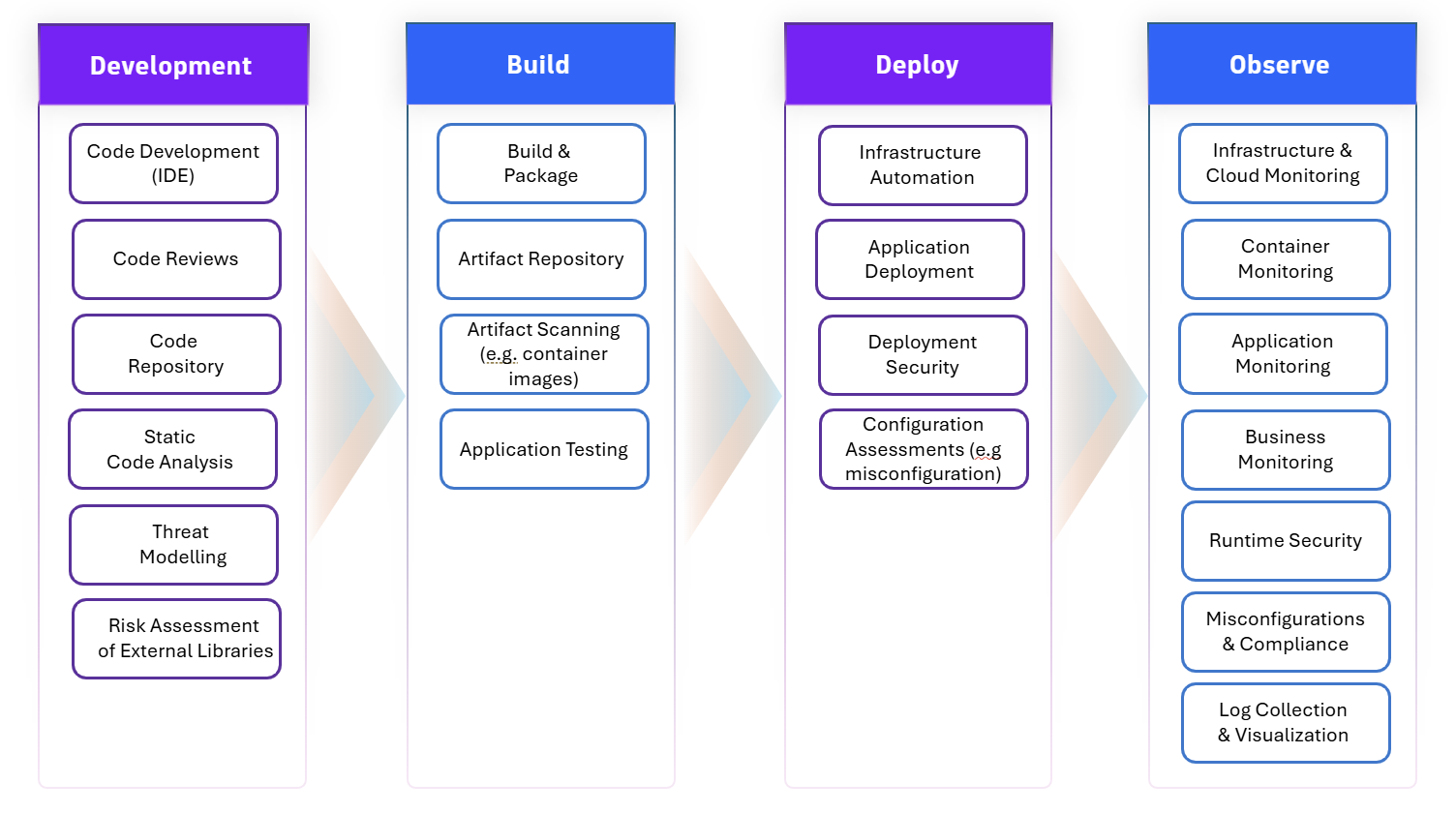
Each phase contributes unique controls and processes to a strong overall security posture. This layered approach is essential for protecting sensitive data, maintaining customer trust and meeting regulatory requirements in an increasingly hostile cyber environment.
To understand how this works in practice, let’s look at an example of a cloud-native microservices application.
End-to-end scenario: How the Astronomy Shop application leverages runtime context
Consider Astronomy Shop, an online retailer demo application built on containerized microservices such as frontend, product, cart, checkout, payment, order, and search — all deployed on Kubernetes. Astronomy Shop’s teams implement defense-in-depth across the SDLC phases to secure their application.
By leveraging runtime context, they validate and prioritize risks in production, ensuring that the most critical security issues are addressed first. Below is a walkthrough of how Astronomy Shop uses tools and Dynatrace capabilities throughout the SDLC to enhance security.
Effective security starts at the foundation: during development. This phase sets the tone for the entire security lifecycle.
Development phase: Build security from the ground up
Scenario: Developers commit code for services like product, cart, and checkout. Security scanning runs early, and threat modeling identifies sensitive paths (e.g., checkout and payment). Findings are triaged later using the runtime context to prioritize risks.
Sample tools:
- SonarQube for code quality and static application security testing (SAST), GitHub Advanced Security for dependency monitoring and software composition analysis (SCA).
The Dynatrace role:
- Ingests security findings from development tools via OpenPipeline’s security events ingest endpoint.
- Maps findings to the Semantic Dictionary in Grail™ for unified prioritization, analysis, and automation.
- Highlights critical and high alerts and deprioritizes non-executed code vulnerabilities while prioritizing medium issues exposed to sensitive data. This helps developers focus on vulnerabilities that pose real risks in production.
After development, the build phase is positioned to catch vulnerabilities before deployment.
Build phase: Strengthening security through automation and testing
Scenario: Astronomy Shop teams build and push container images to AWS ECR. Automated image scanning tools like AWS Inspector and Snyk Container assess vulnerabilities. Findings are enriched with runtime context to identify which issues truly impact production.
Sample tools:
- AWS Inspector for image scanning and Snyk for container scanning.
- Recommended approach: Artifact/container image scanning for OS and package vulnerabilities.
The Dynatrace role:
- Extends observability to the build phase for governance and security hygiene control.
- Adds runtime context to container scans, so developers know which vulnerabilities to prioritize. This simplifies decision making and reduces cognitive load.
- Automates security gates and workflows with tools like Site Reliability Guardian to ensure no critical vulnerabilities affect production.
And now, we move on to deployment, the critical moment when applications face real-world threats.
Deploy phase: Safeguard production with real-time oversight
Scenario: The Astronomy Shop team deploys services to Kubernetes using Helm or GitOps. Admission policies and baseline checks run, while cloud controls enforce guardrails and flag misconfigurations.
Sample tools:
- Kyverno for workload and cluster policies, AWS Security Hub for cloud security posture management (CSPM).
The Dynatrace role:
- Monitors deployment success and audits deployment operations by ingesting SDLC events.
- Enriches KSPM and cloud misconfiguration findings with runtime context to prioritize critical issues.
- Detects and addresses configuration issues with Dynatrace KSPM, ensuring continuous monitoring in Kubernetes and cloud environments.
Once deployed, applications should be actively monitored to detect and address emerging threats and potential signs of compromise.
Observe phase: Monitor production for threats
Scenario: The Astronomy Shop application is deployed to production and actively monitored. A new vulnerability is discovered in a library, and Dynatrace detects and locates the issue in real time. Malicious actors attempt to exploit the vulnerability, but the application remains secure due to proactive patching.
Sample tools:
- Dynatrace Runtime Application Protection (RAP), Runtime Vulnerability Analytics (RVA), Microsoft Defender for Cloud, Amazon GuardDuty, Microsoft Sentinel.
The Dynatrace role:
- Unifies third-party runtime detections and security signals into a single view for efficient processing.
- Provides deep runtime observability through OneAgent, extending visibility to process health, cloud, and infrastructure.
- Enables runtime security capabilities like RVA (Runtime Vulnerability Analytics), Security Posture Management (SPM), and Runtime Application Protection (RAP), serving as the final defense layer against threats.
Figure 3 highlights how Dynatrace integrates seamlessly across the SDLC, enhancing security with runtime context and enabling teams to prioritize and address the vulnerabilities that matter most.
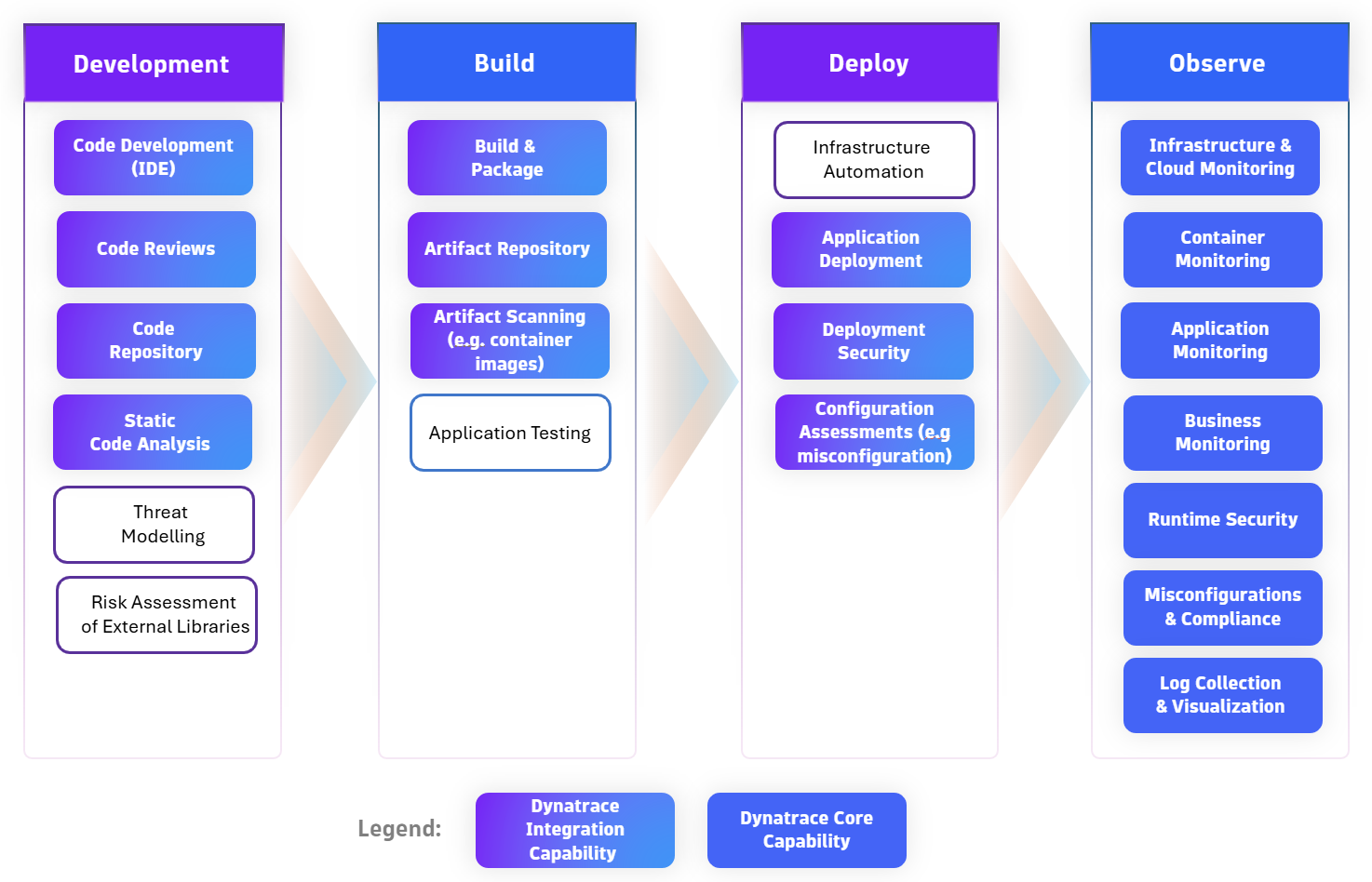
Let’s examine practical scenarios where Dynatrace enhances left-shifted security findings with runtime context, enabling environment-aware prioritization.
Practical scenarios: Elevate security with runtime context
- Prioritize SAST findings in code
Static scanners often detect thousands of vulnerabilities, many of which are irrelevant in production. Runtime context enables teams to prioritize vulnerabilities based on actual risk. For instance, critical severity vulnerabilities in non-executed code could be deprioritized, while medium-severity vulnerabilities exposed to the internet and near sensitive data become high priorities. - Prioritize container scanner findings
Container scans often flag numerous vulnerabilities. Runtime context helps determine whether these issues truly impact production. For example, a critical vulnerability in a library that is never executed in production can be deprioritized, while containers not deployed in production can be addressed later. - Prioritize KSPM findings on clusters
Post-deployment, runtime context helps identify which security issues in workload cluster components or configurations impact production services. Critical vulnerabilities with no direct impact on production can be deprioritized, letting teams focus on what matters most. - Prioritize cloud alerts and compliance findings
Continuous assessment of cloud environments and prioritization of misconfigurations with the application insights reduces the noise from cloud alerts and help to remediate the most important issues first.
Ready to strengthen your security in production?
Explore how Dynatrace can integrate seamlessly into your DevSecOps processes providing application-level insights to security findings across the SDLC for smarter prioritization.
Sign up for a free trial and experience how real-time runtime context makes your organization more secure.



Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum