Today’s organizations face increasing pressure to keep their cloud-based applications performing and secure. Cloud application security remains challenging because organizations lack end-to-end visibility into cloud architecture.
As organizations migrate applications to the cloud, they must balance the agility that microservices architecture brings with the complexity and lack of transparency that can also come with it.
For many IT teams, application vulnerabilities remain a key challenge. According to a recent survey of more than 16,000 respondents, nearly half (47%) worked for organizations that have a backlog of vulnerable applications. Threats to applications can be costly and disruptive. Consider Log4Shell, a zero-day vulnerability that emerged in 2021, affecting millions of applications. Log4Shell required many organizations to take devices and applications offline to prevent malicious attackers from gaining access to IT systems and sensitive data.
At this year’s RSA conference, security pros will explore themes such as the role of automation in cyberthreat detection and the importance of DevSecOps in proactive cybersecurity. Taking place in San Francisco April 24-26, RSA’s theme is “Stronger together.” The focus on bringing various organizational teams together—such as development, business, and security teams — makes sense as observability data, security data, and business event data coalesce in these cloud-native environments.
Indeed, in a recent survey, 88% of respondents say the convergence of observability and security practices is critical to building a DevSecOps culture. As data from different corners of the enterprise proliferates, teams need a better way to bring data together to identify performance and security issues, minimize security risk, and drive greater business value.
Read on to learn more about the ways observability and security are converging and how this affects vulnerability management, real-time response, and the rise of DevSecOps in our RSA 2023 news guide.
Application vulnerabilities remain a key concern
Application vulnerabilities—weaknesses or flaws in software applications that malicious attackers can use to exploit IT systems—exist in any type of software, including web and mobile applications. The CVE Program, which publishes vulnerabilities as they become known, reported a 25% increase in vulnerabilities between 2021 and 2022. As digital transformation escalates, vulnerabilities are increasing as well, by more than 290% since 2016.
As organizations develop new applications, vulnerabilities will continue to emerge. As a result, organizations need to be vigilant in identifying and addressing vulnerabilities to protect their systems and data. Failure to do so can generate significant financial losses, reputational damage, and legal liability. In many cases, organizations don’t discover vulnerabilities until after they have been exploited. This means that attackers may have already gained access to sensitive information or compromised the system.
Open source software is likewise playing a larger role in cloud computing, which brings benefits and dilemmas: bad actors have ready access to open source software and can identify new vulnerabilities to exploit. At the same time, the pervasiveness of open source has also helped expose vulnerabilities and, as a result, made some software flaws easier to detect and fix. For example, the open source Java library at the heart of the Log4Shell crisis in 2021 was patched within days given the pervasiveness of the code. The trick then becomes being able to immediately detect if your organization is affected, how badly, and what systems to remediate first to minimize the effects.
Learn more about managing application vulnerabilities in cloud-native environments from the following resources.
 |
Detect and remediate Log4Shell with Dynatrace – resource center
Discover everything you need to know about Log4Shell and how to easily extend Dynatrace observability to automatically assess and mitigate security risks throughout the SDLC. |
 |
How vulnerabilities are evaluated – platform module
Learn the mechanism that Dynatrace Application Security uses to generate third-party vulnerabilities and code-level vulnerabilities. |
 |
Dynatrace ‘DevSecOps Lifecycle Coverage with Snyk’ eliminates security coverage blind spots – blog
DevSecOps Lifecycle Coverage with Snyk, a new app developed with Dynatrace® AppEngine, enables teams to mitigate security risks across pre-production and production environments, including runtime vulnerability detection, blocking, and remediation. |
 |
Dynatrace Runtime Vulnerability Analysis now covers the entire application stack – blog
Automatic vulnerability detection at runtime and AI-powered risk assessment further enable DevSecOps automation. Learn more. |
 |
What is vulnerability management? And why runtime vulnerability detection makes the difference – blog
Vulnerability management is an essential part of securing IT operations. But managing the breadth of the vulnerabilities that can put your systems at risk is challenging. |
Convergence of observability and security data is a must
As digital transformation accelerates, most organizations house hybrid cloud environments for which observability and security are paramount concerns.
Observability is critical for monitoring application performance, infrastructure, and user behavior within hybrid, microservices-based environments. This includes collecting metrics, logs, and traces from all applications and infrastructure components.
To ensure application security in these hybrid cloud environments, organizations must integrate security into this observability framework. Monitoring potential security threats, such as unauthorized access attempts, malware infections, or data exfiltration, is critical, especially as workloads are distributed across multiple environments.
But organizations face barriers to this convergence. For example, in a recent study, 55% of security teams say they don’t trust developers, and 49% of developers perceive security teams as a blocker to innovation. And 36% of these organizations also reported that the siloed culture between DevOps and security teams prevents collaboration. Teams need a better way to collaborate and build trust while securing their applications and automating DevSecOps.
Learn more about converging observability with security in the following resources.
 |
Global Report Reveals the Need for the Convergence of Observability and Security as Rising Complexity of Cloud-Native Development Exposes Organizations to Heightened Security Risks – press release
81% of CISOs say they will see an increase in vulnerability exploits if they can’t make DevSecOps work more effectively. |
 |
Log auditing and log forensics benefit from converging observability and security data – blog
Cloud complexity challenges log auditing and log forensics. Converging observability and security data provides real-time answers at scale. |
 |
Global CIO Report Reveals Growing Urgency for Observability and Security to Converge – press release
94% of CIOs say extending a DevSecOps culture to more teams is key to accelerating digital transformation and driving faster, more secure software releases. |
 |
RSA 2022: Why modern observability forwards application security objectives – blog
Modern observability platforms have become critical to ‘shifting left,’ and finding code issues in development as well as to ‘shifting right,’ and identifying vulnerabilities in live applications. |
 |
Observability and security must converge as the financial services sector goes cloud-first – blog
A new Dynatrace report highlights key vulnerability management challenges for banks and insurers. |
 |
2022 CISO Report: Retail sector – report
Dive deep into the state of runtime vulnerability management in retail and how to protect your brand. |
 |
Context is king: Converging security and observability to protect a digital-first world – Forbes.com article
Many tools also don’t see deep enough inside cloud-native architectures to quickly pinpoint newly discovered zero-days for patching. If something doesn’t change, organizations will be unprepared when the next Log4Shell emerges. |
 |
What the convergence of observability and security means for devs – DevOps.com article
To help developers build for the future and address security concerns, it is imperative they rethink the way they are collecting, operationalizing, and storing different types of data from a variety of sources. |
 |
Urgency Grows for Observability and Security Convergence – APMdigest.com article
CIOs and senior DevOps managers are looking to DevSecOps processes, the convergence of observability and security, and the increased use of AI and automation to balance accelerated innovation with reliability and security. |
Shifting left and shifting right
DevSecOps practices bring development, security, and IT operations teams closer together to identify infrastructure and applications issues before they affect users, cause downtime, or compromise data.
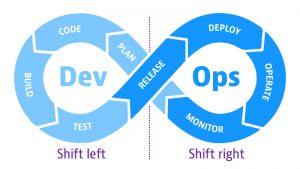
Central to preventing these issues are the practices of “shifting left” and “shifting right.”
Shifting left is the practice of moving testing, quality, and performance evaluation early in the development process, often before code is written. When DevOps teams move these tasks earlier in the development process, it can aid in finding software flaws before they enter production. Shift right refers to testing software in real-world production conditions to ensure it can hold up under load. From a security perspective, this means evaluating software for runtime vulnerability exposure that can’t be detected in a development environment. Shifting left and shifting right also enable DevSecOps teams to create closed-loop systems that are resilient,
DevSecOps teams need to shift left to speed development cycles without compromising quality. They also need to shift right to identify flaws in live applications before they have user or security impact.
At the same time, shifting left and right can nevertheless create silos and hamper productivity. According to a recent survey, even among organizations that have shifted left, 75% of C-suite executives say security challenges limit their ability to innovate. As shifting left becomes a core principle for DevSecOps teams, they need to rely on DevOps automation to ensure higher-quality code and to enable innovation.
Learn more about detecting application security issues in development and at runtime from the following resources.
 |
Shift left vs. shift right: A DevOps mystery solved – blog
Shift-left evaluation reduces defects and speeds delivery in development. Shift-right ensures reliability in production. Together they equal better software. |
 |
Log4Shell highlights the need for secure digital transformation with observability, vulnerability management – blog
The Log4Shell vulnerability highlighted the importance of developing a secure digital transformation strategy. Modern observability, combined with vulnerability management, helped Avisi keep its customers secure as they digitally transform. |
 |
InfoSec 2022 guide: How DevSecOps practices drive organizational resilience – guide
Improving DevSecOps practices and capabilities can increase security resilience. Learn more with the 2022 InfoSec guide. |
 |
Shift-Left with Dynatrace: Automating Performance Feedback with AWS, Mesos and Containers – blog
Andi Grabner had an opportunity to speak with a customer working in the financial sector. He recaps the Shift-Left journey they have taken with Dynatrace. |
DevSecOps: Stronger together
Dealing with the deluge of data in modern cloud environments requires that organizations work smarter, not harder. DevSecOps practices promise to bring development, operations, and security teams together so they can align their efforts on the same goals. But that alignment can be easier said than done.
While there is wide agreement that collaboration drives more successful transformation—94% of CIOs say extending a DevOps culture to more teams is key to driving faster, more secure releases—actually doing it has proved more elusive. Only 27% of those CIOs say their teams fully adhere to a DevOps culture.
Meanwhile, traditional databases have demonstrated limitations in increasingly complex and distributed cloud-native environments. The schema and index-dependent approach of traditional databases can’t keep pace or provide adequate analytics of these hyperscale environments.
One key to augmenting DevSecOps collaboration is to take a platform approach that converges observability and security with big data analytics that can scale without compromising data fidelity.
Check out the following resources to learn more about how teams can facilitate DevSecOps with analytics capabilities that scale with modern environments.
 |
InfoSec 2022 guide: How DevSecOps practices drive organizational resilience – guide
Improving DevSecOps practices and capabilities can increase security resilience. Learn more with the 2022 InfoSec guide. |
 |
What is DevSecOps? And what you need to do it well – blog
What is DevSecOps? DevSecOps connects three different disciplines: development, security, and operations. Learn how security improves DevOps. |
 |
DevOps vs DevSecOps: Why integrate security and DevOps? – blog
Understand the difference between DevOps and DevSecOps. See how incorporating security practices into delivery workflows pays off |
 |
DevSecOps automation improves application security in multicloud environments – blog
DevSecOps automation is essential for ensuring application security in multicloud environments. Learn how to automate DevSecOps at scale. |
 |
The top eight DevSecOps trends in 2022 – blog
From Infrastructure as Code to GitOps and serverless architecture, the top DevSecOps trends in 2022 will continue to enable teams to automate, streamline their CI/CD pipelines, and make time for innovation. |
 |
Good things happen when DevSecOps and cloud collide – DevOps.com article
Increasingly wrapped around microservices, containers, and orchestration platforms, the complexities of cloud expansion and software development couldn’t be more intertwined or expose more complicated risks than they do today. |
 |
Benefits and challenges of DevSecOps for business – DevOps.com article
By automating and integrating security practices into the software development life cycle, development teams can react to vulnerabilities sooner, automate security checks and proceed into production with a more reliable and secure product. |
If you’re at RSA on April 24-26, 2023, come by to meet the Dynatrace team at booth 1261.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum