Dynatrace Blog
Modern cloud done right. Innovate faster and compete more effectively in the digital age.



AWS re:Invent 2022 guide: Cloud application modernization remains key issue

The capabilities government leaders need as they manage the cloud’s data explosion

What is digital immunity? Creating secure, resilient software with observability

What to expect at Amplify PowerUP 2022

Mobile application monitoring with Dynatrace: How an end-to-end platform advances mobile DevOps
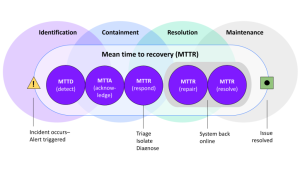
What is MTTR? How mean time to repair helps define DevOps incident management

AIOps and digital transformation modernize BT
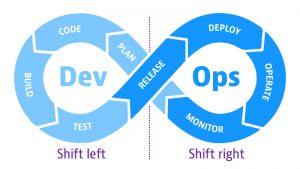
Shift left vs shift right: A DevOps mystery solved

Tailored access management for Dynatrace, Part 1: One configuration for all authorization requirements

Why open source software and open standards are crucial to the future of software development

Dynatrace SaaS release notes version 1.253

Prevent potential problems quickly and efficiently with Davis exploratory analysis

Path to NoOps part 1: How modern AIOps brings NoOps within reach

How OpenFeature — and feature flag standardization — enables high-quality continuous software delivery

New high severity vulnerability, CVE-2022-42889, in Apache Commons Text discovered

OneAgent release notes version 1.251

Applying real-world AIOps use cases to your operations

Metric events: Set up anomaly detection based on your business needs
What is AIOps? An insider’s guide to AI for ITOps — and beyond

Getting answers from data starts with automated log acquisition, at any scale

Dynatrace Managed release notes version 1.252

Dynatrace SaaS release notes version 1.252