
If you ask most people how to secure a web application, you will immediately hear: “Use a web application firewall.” But there is much more to it than that. In this blog, I’ll first cover the basics, explaining what web application security is and why it’s important. Then I will describe various types of security products that can be used for web application security including some innovations that Dynatrace has recently introduced.
What is web application security?
A web application is any application that runs on a web server and is accessed by a user through a web browser. Examples range from online banking to personal entertainment delivery and e-commerce. Because web applications are so common, and so easily accessed by attackers, they have become a common target for attackers. Web application security is the process of protecting web applications against various types of threats that are designed to exploit vulnerabilities in an application’s code.
Good web application security starts when the application is being developed. Application security tests can be used to tell developers when they have introduced vulnerabilities into the application they’re building. Once the application has been deployed, various types of security controls, including the common web application firewall, are designed to defend the application against live attacks. Using the standard DevOps graphic, good application security should span the complete software development lifecycle.
Why is web application security important?
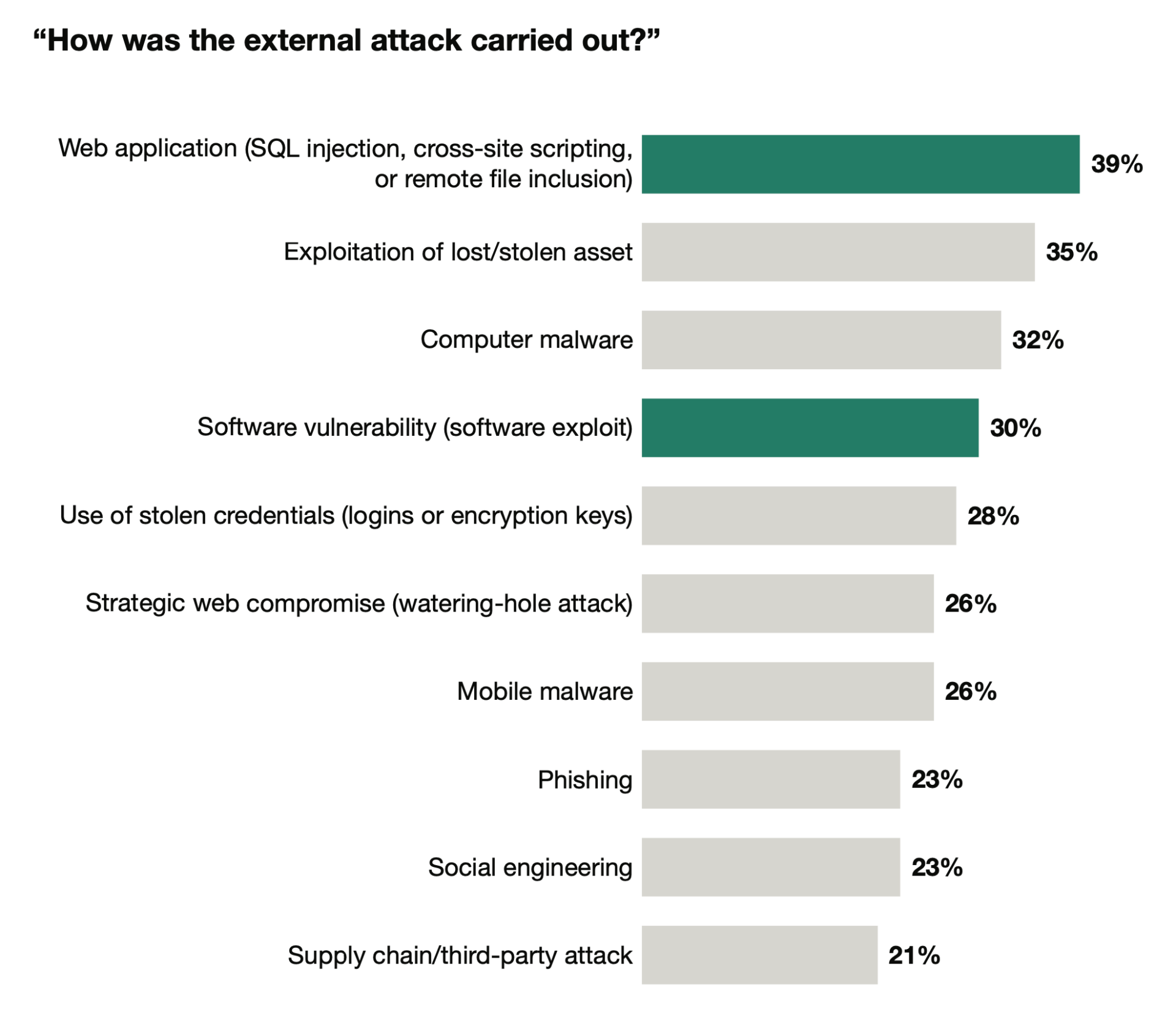
Attacks against web applications are very common. According to the 2019 Verizon Data Breach Investigations Report, web application attacks were the number one type of attack. Data from Forrester Research provides more detail, finding that 39% of all attacks were designed to exploit vulnerabilities in web applications. (Source: “The State of Application Security, 2021”, Forrester Research, March 23, .)
Attacks against web applications can also be very costly. The attacker can leverage the web application to exfiltrate both enterprise information and private customer data. Recent examples include:
- The Equifax data breach, in which the private records of 147.9 million Americans, 15.2 million British citizens, and about 19,000 Canadian citizens were compromised
- The Marriott data breach, in which one of its reservation systems had been compromised and hundreds of millions of customer records, including credit card and passport numbers, were stolen
What are common web application vulnerabilities?
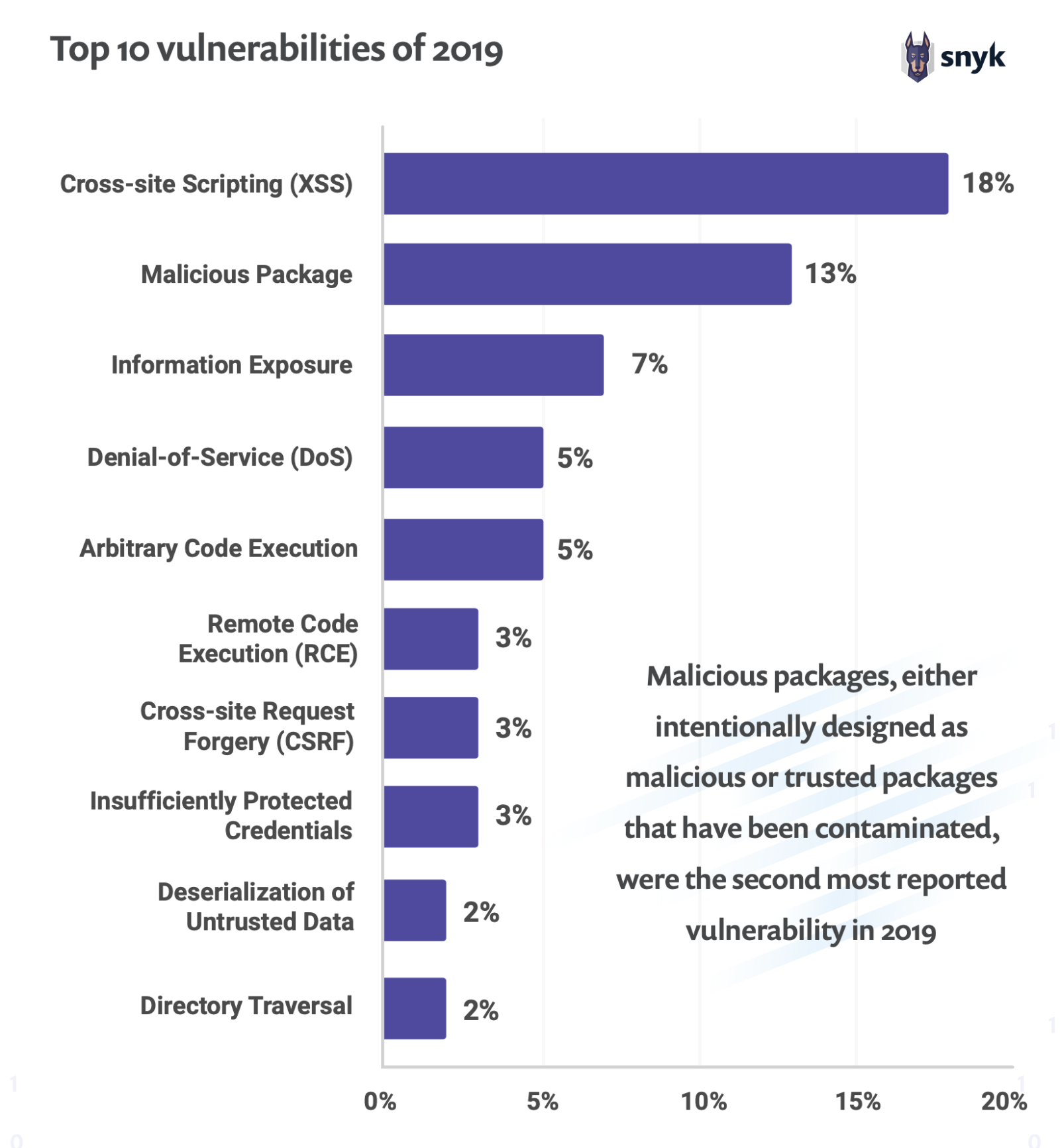
Before one can design an optimal security approach, it helps to understand what kinds of vulnerabilities are commonly present in web applications. Application security firm, Snyk, has researched this extensively. Their “State of Open Source Security Report, 2020” found that the most common vulnerabilities are cross-site scripting vulnerabilities (18%), followed by malicious packages (13%).
Snyk also reports that open-source software is a common entry point for vulnerabilities. Modern applications, on average, comprise 70% of open-source software, the rest being custom code. And open-source software is rife with vulnerabilities.
The need for protection against web application attacks is greater than ever. Especially as software development continually evolves using microservices, containerized architecture, distributed multicloud platforms, and open-source code.
How can web application vulnerabilities be prevented?
Organizations generally use two approaches for web application security: prevent and block. They are not mutually exclusive, and most organizations use both.
Let’s first look at prevention. There are various kinds of tools that can be used to prevent attacks by helping you discover and remediate vulnerabilities in the web application. Below is a list of the most common types.
- Static Application Security Tests (SAST) analyze applications early in the pipeline when they are being written. SAST tools identify problematic coding patterns that go against best practices.
- Software Composition Analysis (SCA) analyzes applications to detect open-source software (OSS) and third-party components known to have security vulnerabilities or licensing restrictions. Both the Heartbleed Bug and Apache Struts vulnerabilities were caused by vulnerabilities in open-source libraries.
- Interactive Application Security Testing (IAST) analyzes applications by observing behavior, including input and output, as well as logic and data flow. Developers include an IAST agent inside each application, and the agent conducts runtime analysis of the application code, memory, and data flow. IAST tools require substantial configuration for each application, and the quality of your configuration determines in large part the quality of the results you will get.
- Dynamic Application Security Tests (DAST) analyze running code, including the underlying application frameworks and servers. To get meaningful results, you need to manually configure DAST for each application you are testing. You can certainly operate a DAST tool with no configuration, and click the scan button, but the results will be limited and likely riddled with false positives.
- Runtime Vulnerability Assessment is a new type of security that has recently emerged. By marrying observability agents with security analytics, Runtime Vulnerability Assessment can give you much more precise risk assessment, because the tools understand how third-party code is (or is not) being used by the application, as well as internet exposures and the business importance of each application.
How can attacks on web applications be blocked?
The two most common types of products that can be used to block attacks are the web application firewall (WAF) and the runtime application self-protection (RASP) tool. Of these, WAF is much more commonly used today. Let’s dive into what each of these are and how they work.
Web Application Firewall (WAF) helps protect a web application against malicious HTTP traffic. By placing a filtration barrier between the targeted server and the attacker, the WAF can protect against attacks like cross-site forgery, cross-site scripting, and SQL injection. WAFs use two methods to block attacks:
- Filters help prevent attacks, such as XSS and SQL injection, from reaching the vulnerable application. The filters are either positive filters, which allow only “known good” inputs to reach the application or negative filters, which block “known bad” inputs. Positive filters are highly effective at blocking attacks but require constant tuning. Teams need to verify and potentially adjust this tuning every time the application changes.
- Transforms add layers of protection to the web application. The most common web traffic transforms implement URL encryption, cookie signing, and anti-CSRF tokens to block CSRF attacks.
Although WAFs are widely used (the PCI DSS regulation requires their use), they are some of the least loved products in the world of security. Here’s how some Gartner analysts describe the current state of WAFs:
“With few exceptions, WAF technology has failed to deliver on the promise to automatically enforce a positive security model.”
“WAF requires high workload capacity and is cumbersome to deploy and operate at scale.”
“WAF appliances have seen little innovation during the past four years.”
(Source: Gartner, Defining Cloud Web Application and API Protection Services, Refreshed May 2020, Published 26 February 2019, Jeremy D’Hoinne and Adam Hils)
Runtime Application Self Protection (RASP) is a technology that leverages in-application instrumentation to detect and block attacks. RASP is a much newer technology than WAF and is deployed either through an SDK that a developer uses to integrate RASP directly into the codebase or through an agent added to the host at runtime. The latter approach is much less invasive to the application development process — there is nothing the developer needs to remember to do. The agent approach also has the advantage of enlarging the potential scope for the RASP deployment; even applications that have not gone through an internal development process can be instrumented by adding the RASP agent to the host at runtime.
RASP offers the potential for very accurate threat detection and blocking because the RASP agent has deep visibility into the running code and libraries. However, early RASP implementations were difficult to install and maintain, resource-heavy, and caused performance stability problems, and therefore did not receive widespread adoption.
The reinvention of web application security
As we announced in 2020, Dynatrace is now applying its Software Intelligence Platform to security use-cases, including web application security through the Application Security module. Dynatrace’s OneAgent makes it easy for customers to operationalize web application security because our Software Intelligence Platform leverages a single agent, OneAgent, that is scalable, easy to maintain, and high-performing. With this converged functionality, multiple teams can leverage the Dynatrace platform for multiple purposes, which makes DevSecOps collaboration an easy reality. The information Dynatrace gathers—such as the actual runtime topology of production environments—can be used for both performance monitoring and risk assessment.
Compared to every other security product on the market, Dynatrace provides a much more accurate assessment of the risk each vulnerability represents to the business. This is done automatically by the Dynatrace AI engine, Davis, which considers the following factors:
- The base Common Vulnerability Scoring System (CVSS) score
- Whether the open-source software package is being used in runtime
- Whether the process is exposed to the Internet
- The number of vulnerabilities exposed by each open-source software package
- Whether each vulnerability could be used to compromise sensitive data
Through this analysis, Dynatrace helps DevSecOps teams focus on the most important risks and remediate them faster than using conventional methods.
Dynatrace is also easier to deploy and operate than other types of web application security products. The Dynatrace OneAgent has been proven to be scalable and high-performing in the largest enterprises in the world. It simultaneously produces information that can be used for performance, reliability, and security purposes. For more information about the Dynatrace platform, check out our product page.


