Application vulnerabilities are a persistent challenge for development teams. The sheer volume of detected CVEs can overwhelm teams, making it difficult to prioritize and remediate effectively.
At Dynatrace, we believe you shouldn’t have to fix every vulnerability. Rather, we believe you should focus on the vulnerabilities that matter to your production environments. That’s why we’ve integrated Dynatrace with Atlassian Rovo Dev to streamline triaging and remediation of critical findings, focusing efforts where they count most.
The challenge of managing application vulnerabilities
Modern applications rely on hundreds of open source dependencies, each potentially introducing security vulnerabilities. Whether it’s a newly disclosed CVE or a long-standing issue in a transitive dependency, these vulnerabilities pose a significant security threat if exploited by malicious actors. Depending on the scale and composition of your applications, you could end up with hundreds of vulnerabilities that apparently need to be addressed.
Static analysis tools detect vulnerabilities in your dependencies and raise alerts. Many of these findings might not pose an immediate threat to production systems—for example, the vulnerable code path might never be executed, or the affected library might not even be loaded at runtime.
Is it possible to get additional validation of vulnerabilities with deeper context into your production services and applications? That would help you understand which vulnerabilities affect your crown jewels and prioritize their remediation over other issues. And is it possible to automate this process while keeping developers in their flow state, thereby reducing context switching and manual analysis of complex security advisories?
This is one of the current dilemmas for development and security teams: how to prioritize remediation without compromising developer velocity or wasting valuable resources on non-critical issues.
Context-aware remediation with Dynatrace and Rovo Dev
The Dynatrace® AI-powered observability platform monitors your applications and provides all the runtime insights required to help organizations navigate hundreds of vulnerabilities and prioritize them using runtime context. Dynatrace Runtime Vulnerability Analytics (RVA) validates whether vulnerable code is actually loaded and executed in production. The Model Context Protocol (MCP) server exposes this deep runtime context to automation and agentic AI-driven workflows.
Atlassian Rovo Dev is an AI-powered coding assistant that can live in your IDE or CLI, or in Jira and Bitbucket on the web. Rovo Dev serves as a developer’s assistant, understanding your codebase and applying fixes, creating pull requests, and managing Jira tickets—all through natural language conversation.
To further streamline and connect the dots, Dynatrace natively integrates with Jira for ticket management and Bitbucket for source control. This allows developers to fine-tune triage and enrichment to their particular needs, leveraging Dynatrace Workflows as the automation engine when needed.
In the following sections, we’ll look at a use case with two scenarios that demonstrate how detection, triage, and remediation of application vulnerabilities are made more efficient using Dynatrace and Atlassian’s latest advances in AI-assisted development.
Intelligent remediation in action
This use case starts with vulnerabilities detected by Dynatrace Runtime Vulnerability Analytics. In this first scenario, a developer retrieves critical vulnerabilities using Rovo Dev in their IDE and verifies them with Dynatrace using the Dynatrace MCP server, then proceeds to fix the vulnerability, create a pull request, and manage the Jira ticket—all without leaving their IDE.
In the second scenario, the initial validation is automated with Dynatrace Workflows, and a Jira ticket is created automatically. The developer then picks up the ticket directly in Rovo Dev and completes the remediation cycle.
By combining Dynatrace deep observability with Rovo Dev intelligent automation, teams can triage vulnerabilities based on actual runtime impact. Instead of treating every CVE as equally urgent, this solution helps prioritize those vulnerabilities that pose real risks to business-critical applications. This not only reduces alert fatigue but also ensures that remediation efforts are focused, efficient, and aligned with operational priorities.
This results in a streamlined, proactive security posture rather than a reactive one. Teams can move faster, reduce manual overhead, and maintain a higher level of confidence in their application security while keeping developers in their flow state.
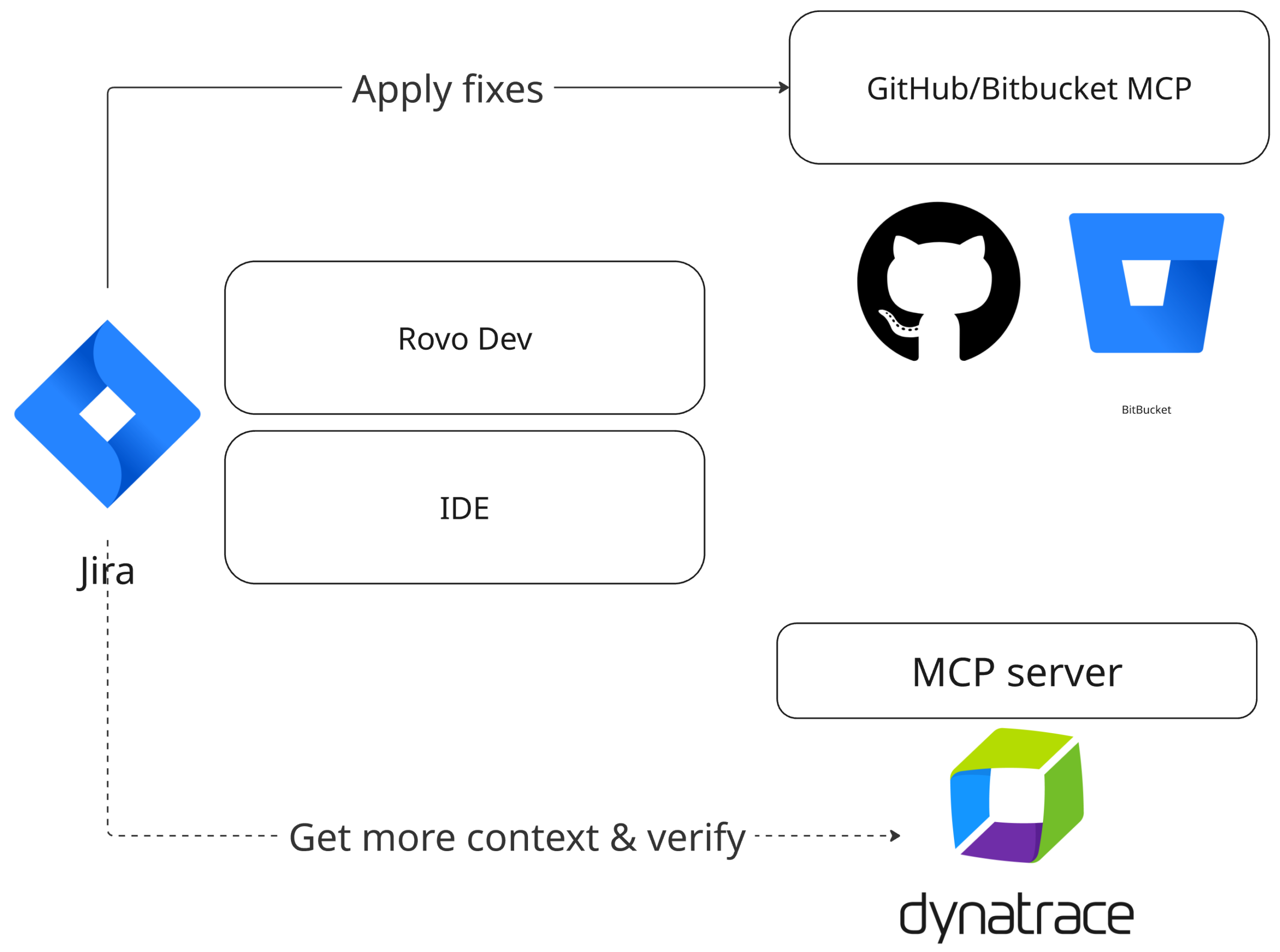
Scenario 1: Rovo Dev-driven validation with Dynatrace MCP
In this scenario, a developer interacts with Rovo Dev to perform validation and remediation actions using Dynatrace MCP.
Detection
Dynatrace Runtime Vulnerability Analytics identifies vulnerabilities in production applications.
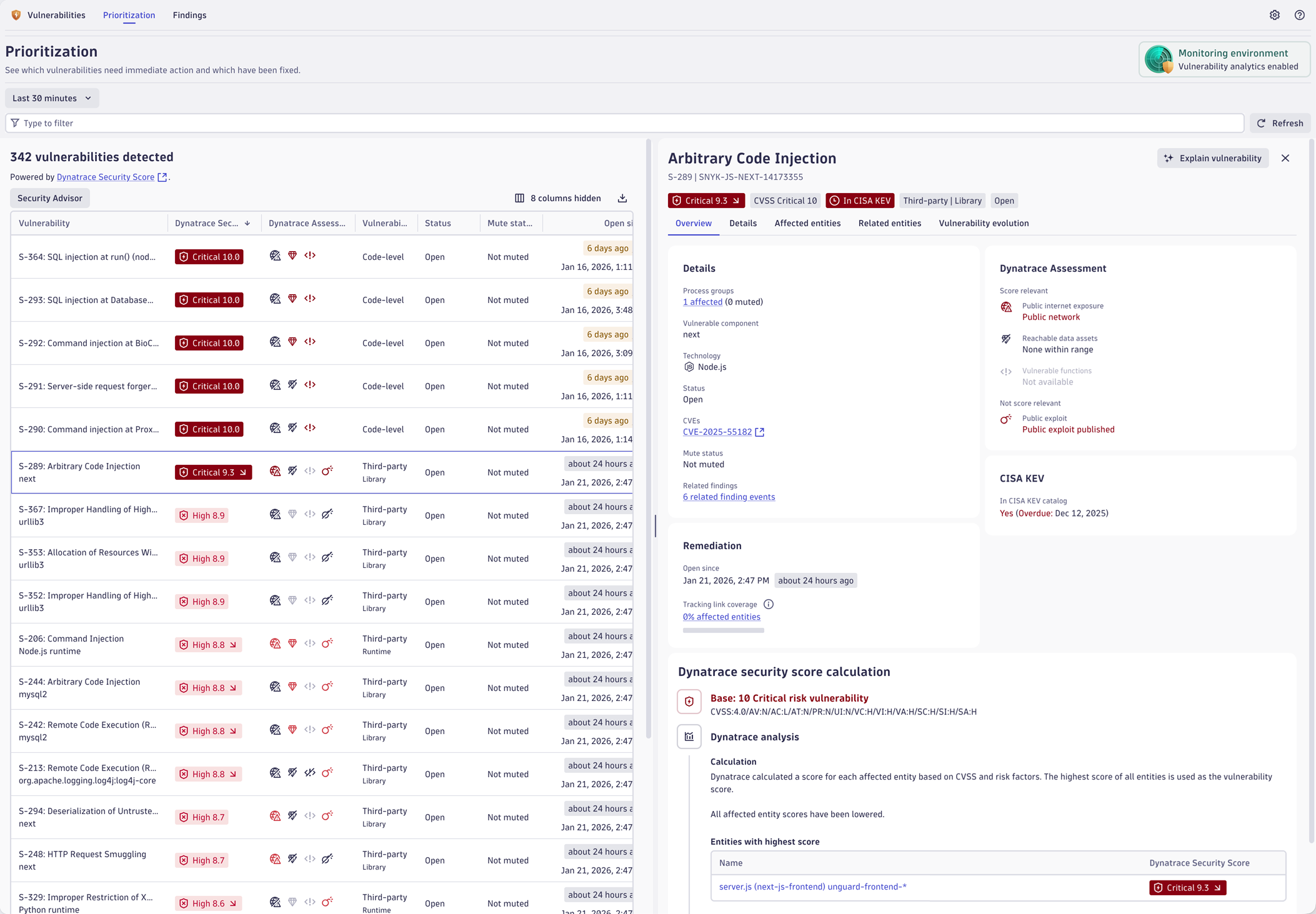
Verification
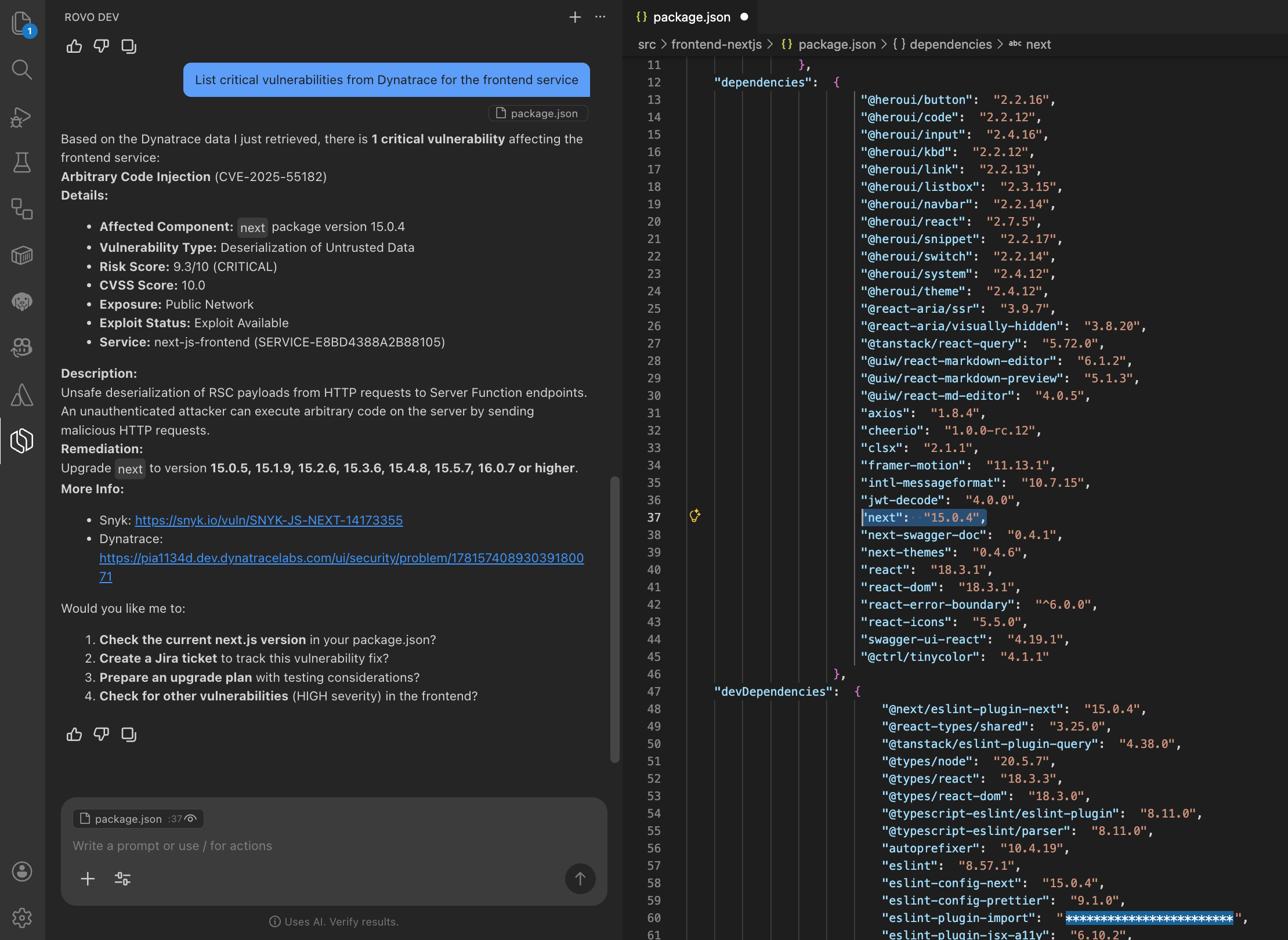
In this phase, the developer invokes Rovo Dev in their IDE and queries Dynatrace for critical vulnerabilities for the relevant service (for example, List critical vulnerabilities for the profile-service).
Rovo Dev utilizes the Dynatrace MCP server to retrieve runtime-validated vulnerability details, including affected services and remediation guidance.
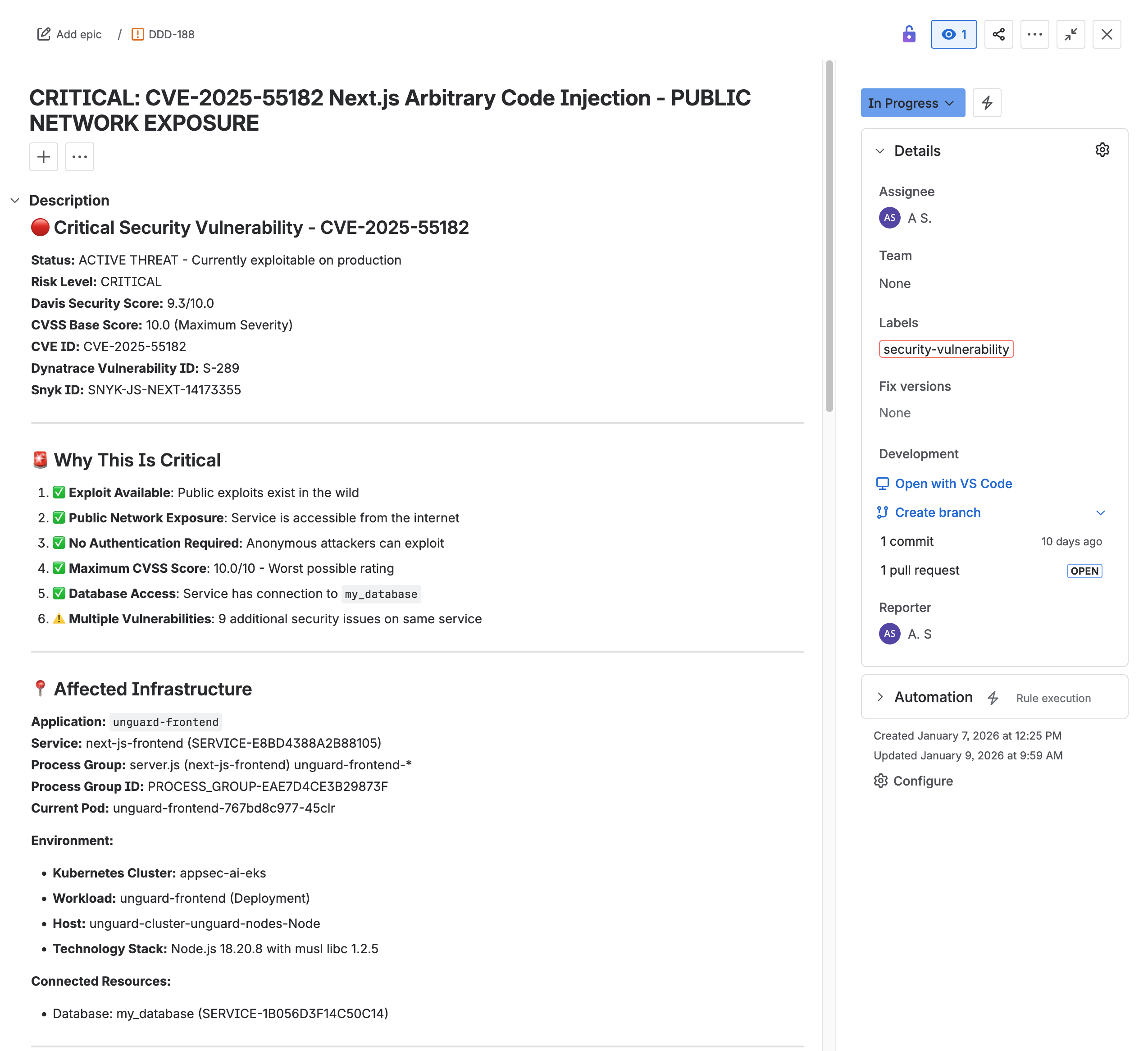
Ticket management
In this phase, the developer uses the Rovo Dev conversational interface to create a Jira ticket for the confirmed vulnerability.
Rovo Dev then checks for existing tickets to avoid duplicates before creating a new ticket with full context from Dynatrace.
Remediation
With the Jira ticket as context, the developer instructs Rovo Dev to apply the fix, run tests, and create a pull request.
Rovo Dev analyzes the codebase, updates the affected dependency, and runs tests.
Rovo Dev then creates a Bitbucket pull request with the fix and links it to the Jira ticket.
The Jira ticket is updated with the PR link and transitioned to the In Review state.
Resolution
Ultimately, developers review and merge the pull request, and the vulnerability is resolved in production. After the application is updated, the user can verify in Dynatrace RVA (or via a Rovo Dev prompt) that the vulnerability has been resolved.
Scenario 2: Dynatrace-driven automated triaging and Rovo Dev remediation
In this scenario, initial validation and triage are automated in Dynatrace Workflows, and the developer then acts on the Jira tickets to perform assisted remediation using Rovo Dev.
Detection– Dynatrace Runtime Vulnerability Analytics identifies vulnerabilities in production applications.
Verification– A workflow verifies the vulnerabilities in production applications using the Dynatrace runtime context.
Ticket management – A Jira ticket is automatically created with a summary of the verification results, including CVE details, affected services, CVSS scores, and remediation guidance.
Remediation – A developer receives the Jira ticket notification and opens the affected repository in their IDE.
Rovo Dev loads the Jira ticket as context, providing full vulnerability details.
The developer instructs Rovo Dev to apply the fix, create a Bitbucket PR, and update the ticket—all in a single conversational flow.
Resolution – Ultimately, developers review and merge the pull request. The vulnerability is resolved, and the Jira ticket is closed.
Solution summary
This integration reduces context switching and alert fatigue by focusing developers on vulnerabilities that actually impact production, transforming a multi-tool, multi-hour process into a seamless conversational workflow.
What’s next
As AI capabilities evolve, the collaboration between Atlassian and Dynatrace will extend to additional use cases for agentic AI workflows and observability-context-supported issue remediation. Beyond vulnerability management, the integration supports:
Incident response: Query active problems from Dynatrace, get root cause analysis, and create incident tickets in Jira with full observability context.
Performance optimization: Retrieve slow transaction data and service dependencies to inform optimization efforts, all from the IDE.
Observability context for existing tickets: For any Jira ticket, query Dynatrace for related logs, traces, metrics, and entity relationships to accelerate troubleshooting.
Recommended blog posts and announcements
For more insights into Dynatrace automated workflows and vulnerability remediation, have a look at these articles:
- Troubleshooting Easytrade with Dynatrace MCP and Gemini CLI
- Write the future: Create your own agentic workflows
- From code to cloud: Dynatrace launches first GitHub custom agent, consolidating observability for developers
Get started
For details on how to set up this use case, please refer to Dynatrace documentation.
Sign up for the preview to learn more about Dynatrace MCP and experience how real-time production context makes your organization more efficient.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum