Identity federation is a mechanism that allows users to access multiple systems or applications using a single set of credentials. It works by establishing a trusted connection between your user identity provider (which authenticates users) and a service provider (which grants access to secure services), thus facilitating single sign-on (SSO).
With the introduction of Flexible Identity Federation, Dynatrace gives its enterprise customers additional options that offer enhanced granularity to match their more complex scenarios.
Scaling with Flexible Identity Federation
Identity federation plays a critical role in modern IT infrastructure, serving as a foundational component that enables seamless, secure access to various systems and applications across different domains and platforms. At its core, identity federation allows users to authenticate once and gain access to multiple systems without the need for repeated logins. This mechanism is crucial in today’s diverse and interconnected digital landscape, where organizations leverage a mix of on-premises deployments, cloud-based services, and third-party applications.
At Dynatrace, we see identity federation as a crucial component of our overall Identity and Access Management strategy, providing centralized identity management, single sign-on, and ultimately, enhanced security. As our customers continue to embrace digital transformation, the need for scalable and flexible identity federation within our platform is apparent.
While Dynatrace Global Identity Federation is adequate for many of our enterprise customers, others have more complex user identity landscapes. These customers often subscribe to multiple Dynatrace accounts to better reflect their business operations based on geographical areas, departments, or other logical groupings. Extending observability data access to their partners or consultants is another important use case for such customers.
Dynatrace Flexible Identity Federation extends the currently available configuration options to include federation at the Dynatrace account or environment level.
Enhance authentication: From global to flexible identity federation
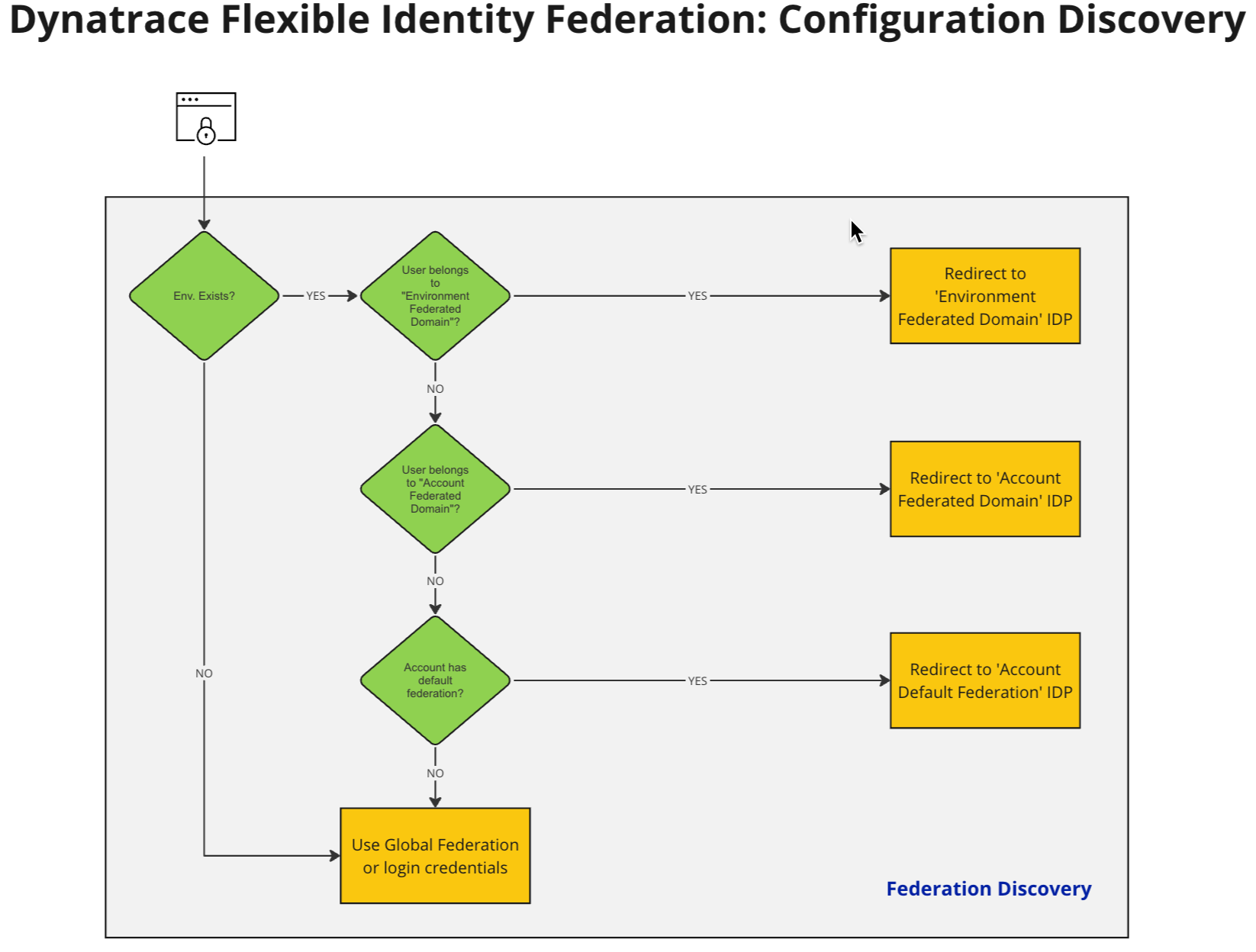
Our established Global Identity Federation works by identifying the domain part of the user’s email address during the login. If SAML Identity Federation was previously configured for the domain, the authentication request is forwarded to the URL of the configured Identity Provider (IdP).
This acts as a catch-all federation that forwards all user authentication requests from a given ownership-verified domain to the previously configured IdP. This configuration applies globally. (This might not be sufficient if you don’t want all user authentication requests forwarded to one IdP.)
Take, for example, a fictitious enterprise customer, ACME Inc., which operates in North America and Europe, with departments and teams in each region working on separate projects without sharing their observability data.
ACME Inc. subscribes to two separate Dynatrace SaaS accounts, one for each region, and wants to route authentication requests to the two individual IdPs they have deployed. Furthermore, the European operations handle most of the systems development and would like to allow software developers connecting to a dedicated Dynatrace environment to authenticate through another dedicated IdP.
Flexible Identity Federation expands Global Identity Federation and enables the routing of ACME user authentication requests from the acme.com domain to different identity federation configurations based on their Dynatrace accounts or environments.
Configure identity federation in Dynatrace
With Flexible Identity Federation, you now have configuration options at three Dynatrace platform levels, which allows you to enable multiple configurations simultaneously. These options, which are listed below, are accessible at Identity & Access Management > SAML configuration in your Dynatrace myaccount portal.
- Account – The scope is limited to a particular Dynatrace account.
- Environment – The scope is limited to a particular Dynatrace environment.
- Global – The scope is global, meaning the identity federation configuration will be applied to all users sharing the same domain name, independent of which Dynatrace accounts or environments the users have access to.
See Dynatrace Documentation for full details.
With each level, Dynatrace continues to rely on the domain part of the user’s email address (and potentially other available contextual information) to determine which configuration to use.
Returning to our example above, ACME Inc. could configure the two Dynatrace accounts for North America and Europe to point to their two respective IdPs, while ACME Europe could additionally configure a separate Dynatrace environment under their account to allow their software developers to authenticate through their third IdP. Dynatrace SSO services implement the following Federation Configuration Discovery flow to determine which configuration would apply for a given user.
Account Federated Guest users
Imagine that ACME Inc. wants to extend access to its Dynatrace North American account to its business partners and consultants, logging in using ACME’s IdP but with different domains from ACME’s.
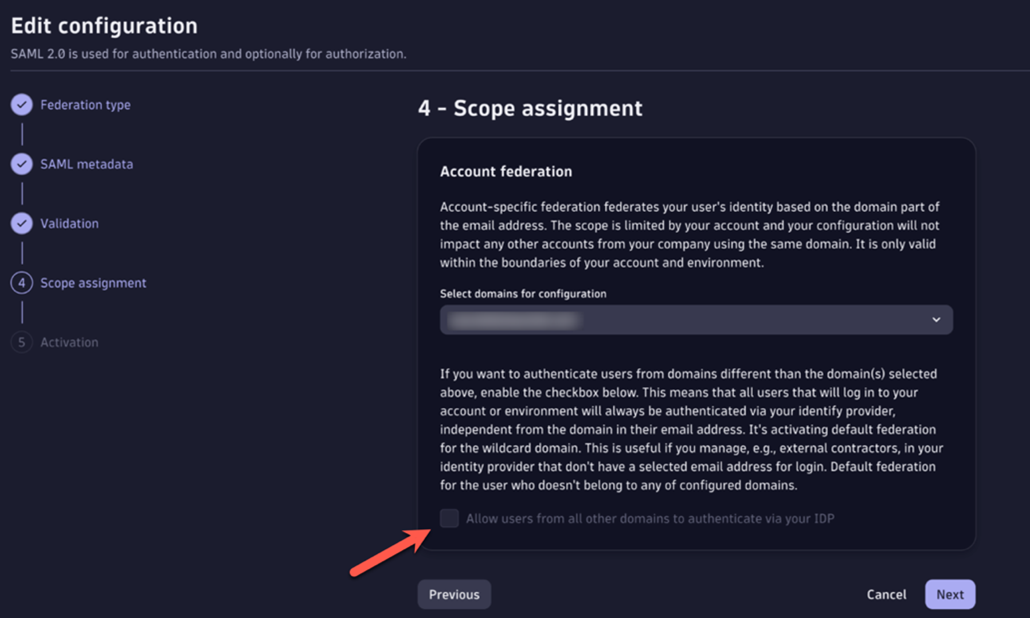
It’s possible to do this as part of your identity federation configuration when you enable the setting Allow users from other domains to authenticate via your IDP as shown in the screen capture below. If enabled, you have already configured Account Default Federation. We refer to such users as “Account Federated Guests.”
In such a configuration, ACME Inc.’s administrator does not need to verify ownership of the external domains.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum