Dynatrace has enhanced its runtime vulnerability analytics by integrating data from the Cybersecurity & Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog, complete with critical remediation due dates. This powerful addition allows organizations to prioritize actively exploited vulnerabilities, align with federal security standards, and focus remediation efforts where they matter most—on threats that attackers are weaponizing right now.
The challenge of vulnerability prioritization
In today’s threat landscape, security teams face an overwhelming challenge in determining which vulnerabilities pose the greatest risk to their organization. With thousands of new vulnerabilities discovered each year, traditional scoring systems like the Common Vulnerability Scoring System (CVSS) often fall short of providing the real-world context needed for effective prioritization.
The reality is that not all vulnerabilities are created equal. While a vulnerability might receive a high CVSS score based on its theoretical impact, it might never be exploited in the wild. Conversely, some vulnerabilities with moderate scores are favorite tools of threat actors and are often involved in widespread attacks and significant business impact.
This disconnect between theoretical risks and actual threats creates several challenges for organizations:
- Resource allocation inefficiencies: Teams spend valuable time patching vulnerabilities that might never be exploited, while more dangerous threats remain unaddressed.
- Alert fatigue: Security professionals become overwhelmed by the sheer volume of vulnerability notifications, which leads to critical issues being missed.
- Compliance gaps: Organizations struggle to align their security practices with federal standards and regulatory requirements.
Enhanced Vulnerability Management with CISA KEV
Dynatrace already provides a Davis Security Score, an enhanced risk-calculation score that’s based on the industry-standard CVSS. Davis® AI provides this precise risk-assessment score by considering additional parameters such as public internet exposure and whether or not data assets are reachable from an affected entity.
Now, Dynatrace has further enhanced its runtime vulnerability analytics by integrating data from the CISA KEV catalog, including the critical due dates for remediation. This addition brings a new layer of actionable intelligence to vulnerability management by unlocking the ability to prioritize actively exploited vulnerabilities.
Unlike general vulnerability databases, KEV is based on real-world exploitation data and expert analysis. Each entry is carefully vetted and includes a due date by which federal agencies must remediate the issue. This due date is not arbitrary—it reflects the urgency of the threat and the need for swift action. By aligning with KEV, Dynatrace helps organizations stay ahead of attackers by focusing on vulnerabilities that are not just theoretical but actively weaponized.
The KEV catalog is especially valuable because it’s curated by cybersecurity experts at CISA using intelligence from government, industry, and open source reporting. Customers integrating KEV into their security workflows can align with federal standards, improve risk-based prioritization, and reduce exposure to high-impact attacks.
KEV filtering and prioritization
Once you’ve turned on runtime vulnerability analytics in Dynatrace, you can filter KEV vulnerabilities in the Vulnerabilities app. The resulting view is sorted based on the remediation due date, starting with the most urgent vulnerability.
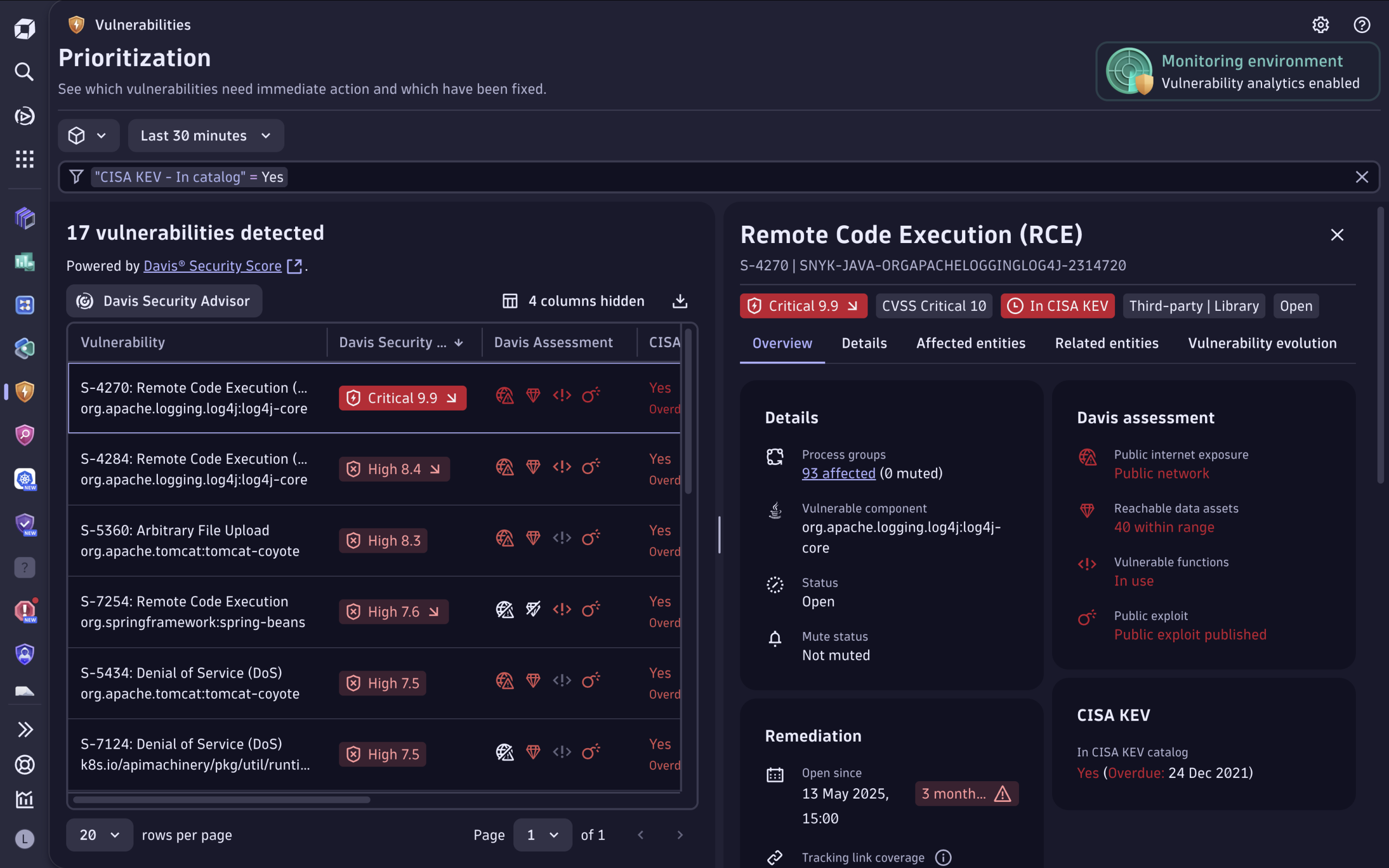
Expanding KEV support
CISA KEV data is available directly within the Vulnerabilities app, giving your teams immediate visibility into the known exploited vulnerabilities that affect their environment and the remediation date by which they must be resolved. In the future, Dynatrace will expand support for KEV data to vulnerability dashboards and automation workflows so you can visualize KEV-related risks in your custom dashboards or assign remediation tasks based on KEV due dates or exploit status.
Try KEV filtering today
This integration helps organizations align with federal security standards, improve risk-based prioritization, and reduce exposure to high-impact attacks. It’s a practical way to stay ahead of cybersecurity threats by focusing on vulnerabilities that are actively exploited.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum