Dynatrace integrates with Amazon GuardDuty to unify, visualize, and automate security findings across tools and environments in a single observability platform built for cloud native and AI workloads. This integration empowers SREs and security teams to understand runtime context for smarter and more efficient threat detection, prioritization of findings, and faster issue remediation.
Observability context is critical to prioritizing Amazon GuardDuty findings
Security remains top of mind for enterprises as the tech landscape continues to evolve, making threat detection and monitoring one of the most critical aspects of an organization’s IT strategy. Amazon GuardDuty is a threat detection service that continuously monitors an organization’s AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation.
Amazon GuardDuty monitors and analyzes events and logs from various AWS services, spanning the entire cloud infrastructure, including running containers in an AWS environment.
However, teams operating in multicloud environments need more than traditional monitoring can provide. To effectively address security issues, teams need a unified monitoring platform to prioritize and efficiently respond to various threats.
Moreover, findings can come from various types of environments, including development, testing, and production. This increases the number of findings to prioritize, increasing the amount of noise, along with the probability of missing critical issues.
Additional runtime and organizational context are required to efficiently filter out the less important findings and focus on the critical issues that directly affect sensitive services and applications.
Reduce alert noise and prioritize critical issues with runtime context
The Dynatrace AI-powered observability platform integrates with Amazon GuardDuty to bring its valuable security findings into the Dynatrace Grail® data lakehouse.
Leveraging OpenPipeline®, the integration processes and maps security findings to a unified data format, making it uniformly accessible for analysis across tools and cloud environments.
Platform-native Dynatrace® Apps, such as Dashboards, Notebooks, and Security Investigator, help you visualize and analyze your security findings. The Workflows app, meanwhile, helps you automate your response—efficiently triaging the findings, creating tickets for DevSecOps teams, and notifying the relevant stakeholders without manual intervention that could slow down the distribution process and tie down your resources.
The Threats and Exploits app serves as your starting point for consuming the ingested findings and as a guide for exploring the potential impact of each detection.
Additionally, Dynatrace allows teams to contextualize ingested security findings with the additional runtime context. This context helps to better filter incoming findings and further reduce the number of alerts handled by various security teams. This way, teams stay focused on the issues that really matter to your critical services and applications.
Breaking down the Amazon GuardDuty and Dynatrace integration
The Amazon GuardDuty integration leverages Amazon EventBridge and AWS Lambda as the transit points for forwarding the various security findings to Dynatrace. The ingested events are processed in OpenPipeline, mapped to Dynatrace semantic conventions, and stored in Grail in a unified security event data model.
The integration provides easy-to-follow steps for setting up the integration and monitoring capabilities to ensure the integration runs properly.
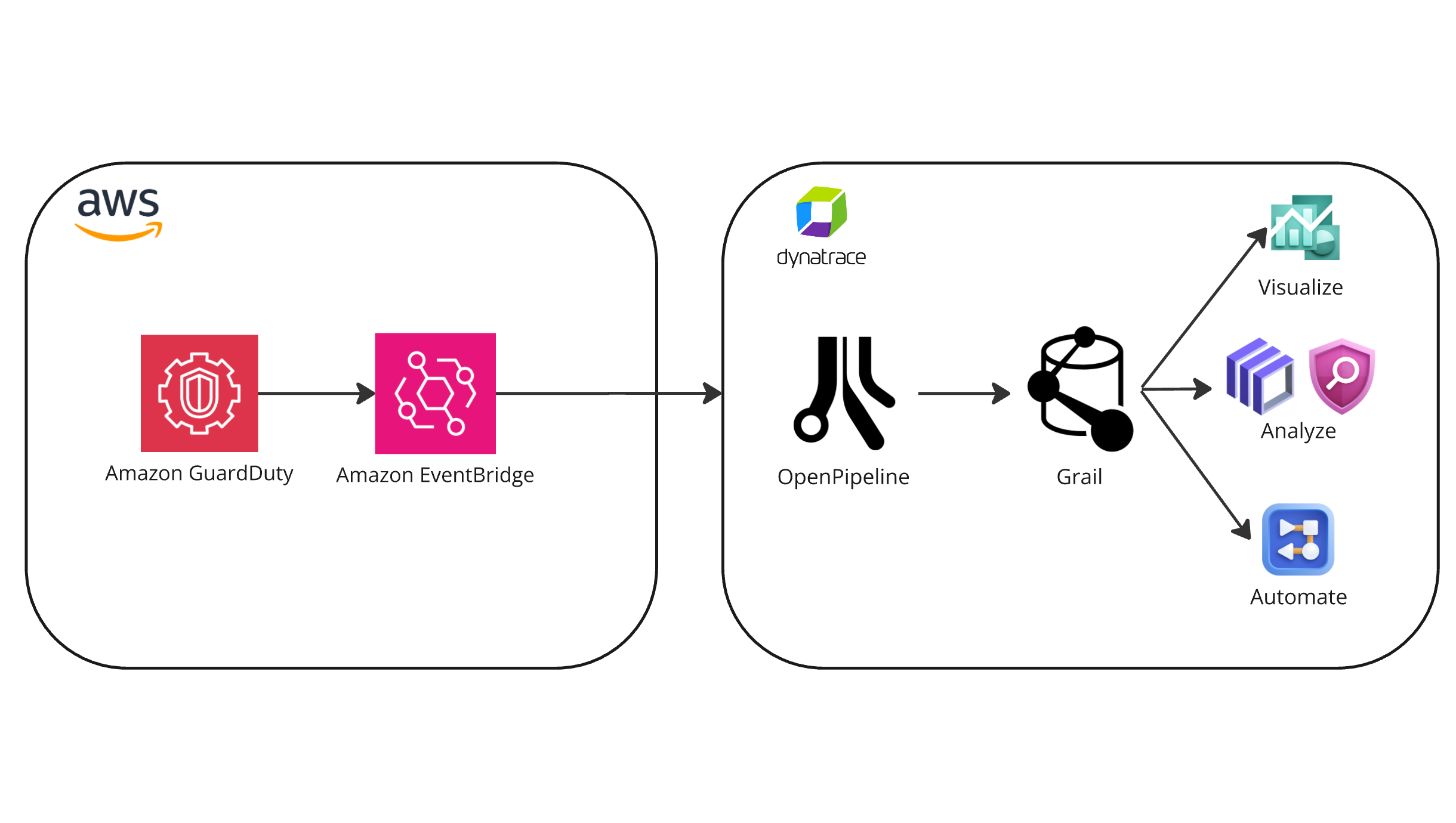
Teams can easily access the ingested security findings using various platform-native apps that help them accomplish various use cases.
Dynatrace also provides several ready-made artifacts as part of the application to serve as a starting point for analysis and automation, including the following:
- Sample dashboards visualize your security findings and assess monitoring coverage.
- Sample workflows automate the orchestration of critical findings by creating notifications and tickets.
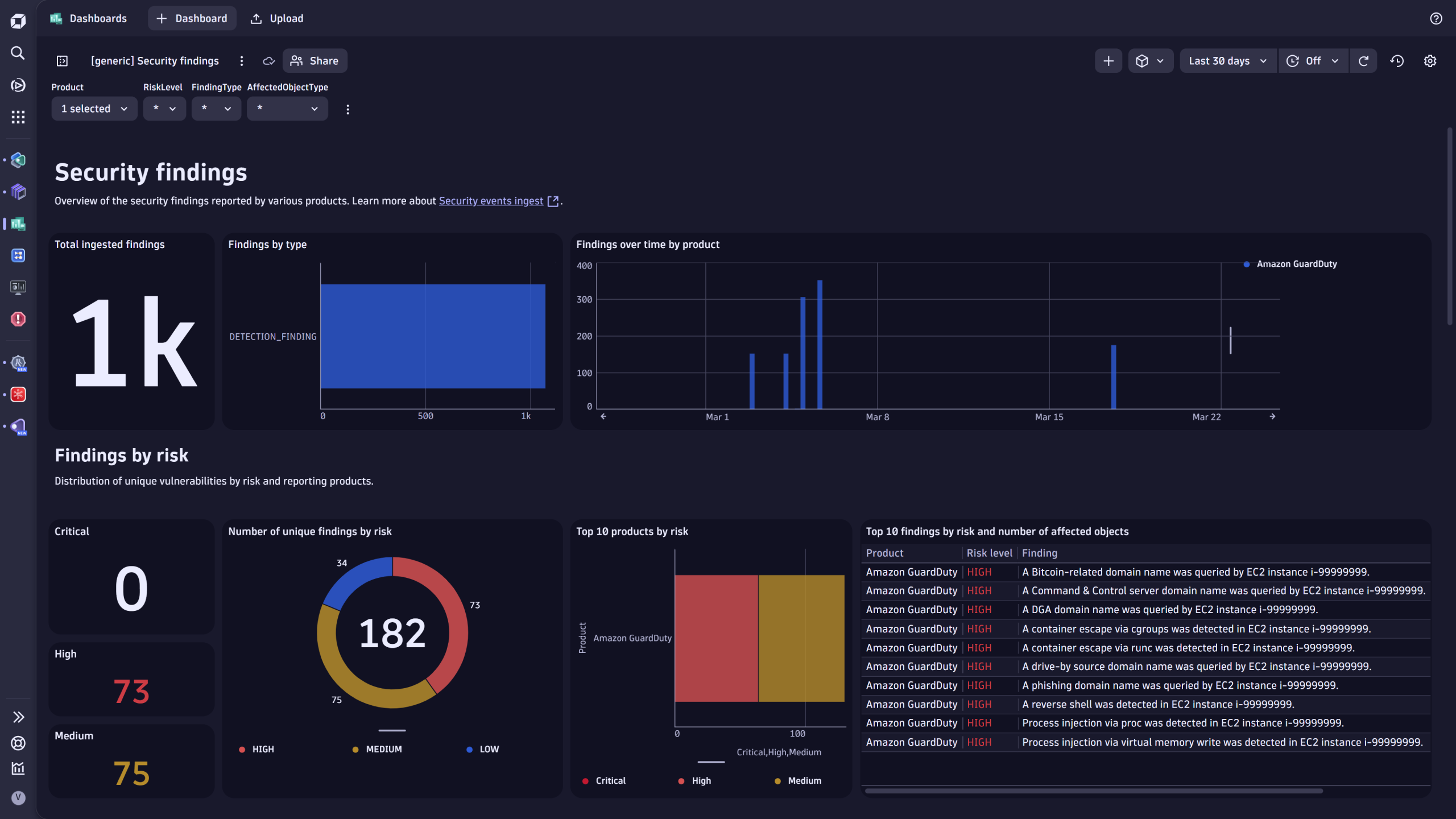
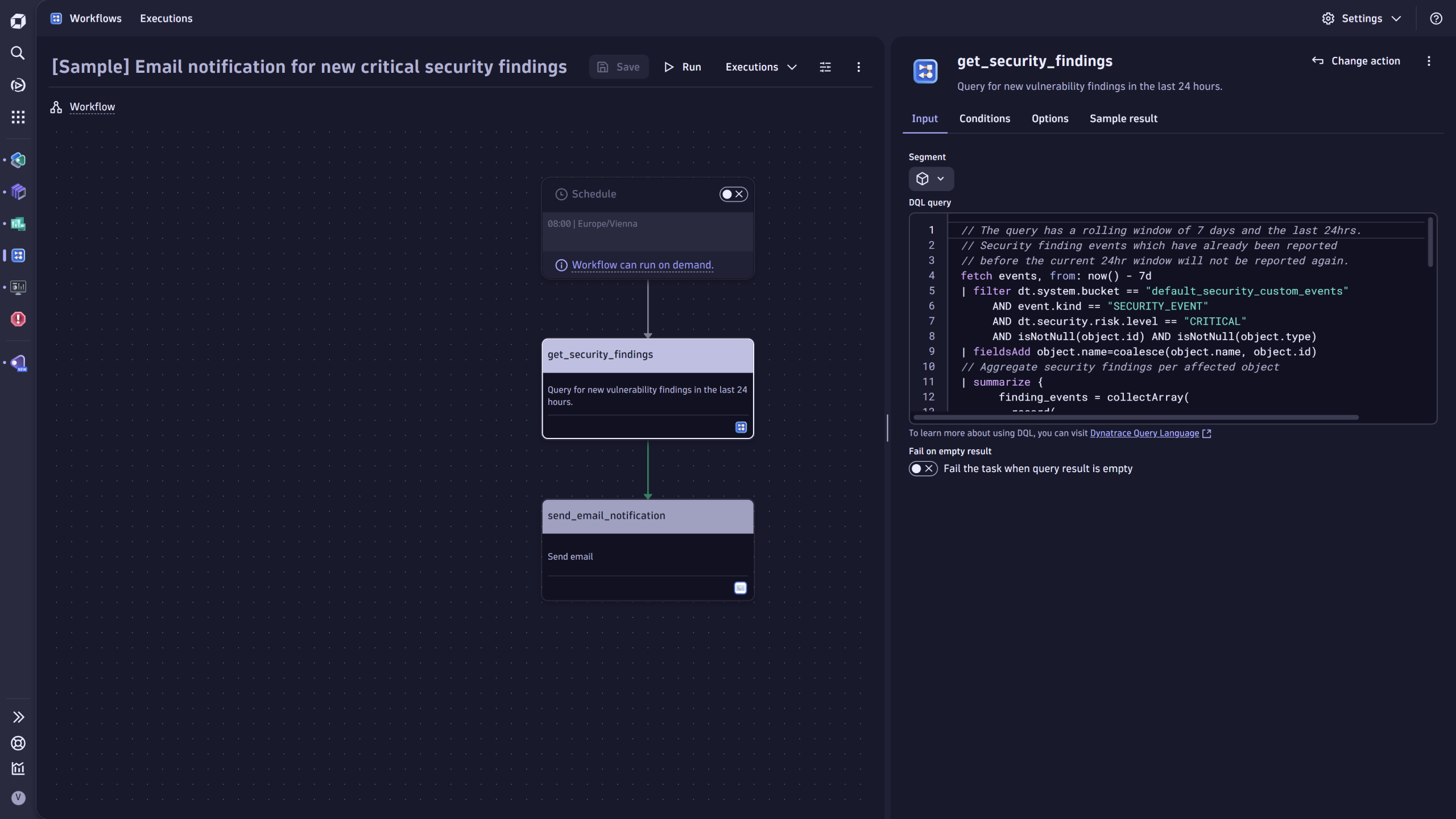
Take the next step with Dynatrace and Amazon GuardDuty
With Dynatrace AI-powered observability context added to Amazon GuardDuty findings, SRE and security teams can now filter out noisy alerts and focus their efforts on the most impactful critical issues.
As the Amazon GuardDuty integration evolves, it will provide additional context that’s mapped and easily accessible in Dynatrace Query Language and available in the Threats and Exploits app.
For more information about how to ingest Amazon GuardDuty security findings, check out our documentation.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum