Application Security overview
After you activate Application Security, assign permissions, and enable and configure Dynatrace Runtime Vulnerability Analytics, Dynatrace starts monitoring your applications to detect vulnerabilities. Go to Security Overview for an overview of vulnerabilities in your global environment.
For security reasons, access to this page is restricted to users who are part of the Security admin group for the whole environment, not just for a selected set of management zones.
The Application Security overview page displays the following information.
Vulnerability count
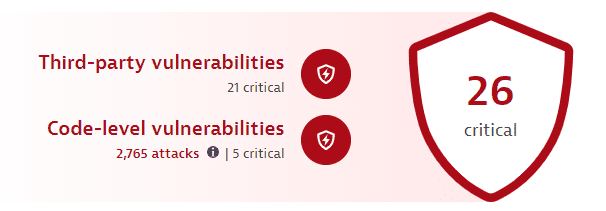
The infographic at the top of the page is based on calculations that take place every 15 minutes and shows
-
In the foreground, the total count of the most severe open vulnerabilities in your environment (
26 criticalin the example above). -
Third-party vulnerabilities: The number of the most severe open critical third-party vulnerabilities (
21 criticalin the example above). Select it to go to Third-Party Vulnerabilities filtered by the highest risk level and the open status.This feature isn't displayed if third-party vulnerability detection is disabled.
-
Code-level vulnerabilities:
-
The number of open code-level vulnerabilities (
5 criticalin the example above). Select it to go to Code-Level Vulnerabilities filtered by the open status.This feature isn't displayed if code-level vulnerability detection is disabled.
-
The total number of attacks—exploited, blocked, and allowlisted (
2,765 attacksin the example above)—that occurred over the last 30 days. Select it to go to the unfiltered Attacks.This feature isn't displayed if Application Protection isn't activated and enabled.
-
Risk level
Vulnerabilities
Host coverage
The Host coverage section shows the coverage of hosts on which vulnerability detection is enabled, based on your settings. This helps you determine where there are coverage gaps and how this can relate to the current number of open vulnerabilities in your environment.
Related resources:
Affected process groups
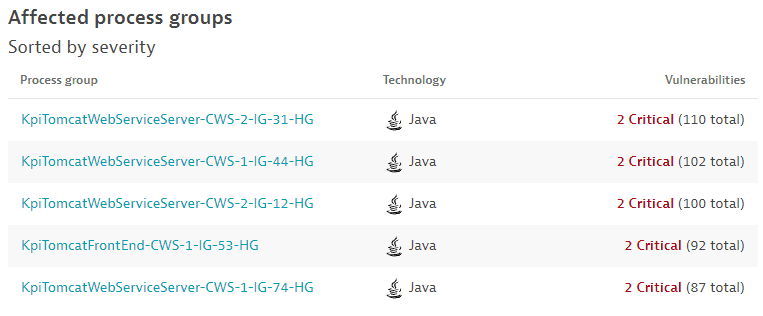
The Affected process groups section shows the top five process groups affected by third-party vulnerabilities, sorted by
The severity of the vulnerabilities affecting the process group.
The number of vulnerabilities affecting the process group.
This section isn't displayed if third-party vulnerability detection is disabled.
The following information is provided.
The name of the process group with a link to the associated process group details page.
The corresponding technology.
The number of vulnerabilities affecting that process group out of the total number of vulnerabilities related to it.
For deeper insights, see Manage third-party vulnerabilities.
Technology coverage
Frequently asked questions
-
On the risk-level chart, how many third-party vulnerabilities are counted in one day if their risk level changes several times that day (for example, from
MediumtoHigh, and back toMediumagain)?- The vulnerability is counted twice, once for
Mediumand once forHigh.
- The vulnerability is counted twice, once for
-
On the risk-level chart, how many third-party vulnerabilities are counted in one day if the affected process is restarted several times that day, but the vulnerability risk level stays the same (for example,
Medium)?- The vulnerability is counted one time, as
Medium.
- The vulnerability is counted one time, as