Process groups anomaly detection API - PUT configuration
Updates the configuration of anomaly detection for the specified process group.
The request consumes an application/json payload.
| PUT | ManagedDynatrace for Government | https://{your-domain}/e/{your-environment-id}/api/config/v1/anomalyDetection/processGroups/{id} |
| SaaS | https://{your-environment-id}.live.dynatrace.com/api/config/v1/anomalyDetection/processGroups/{id} | |
| Environment ActiveGate | https://{your-activegate-domain}:9999/e/{your-environment-id}/api/config/v1/anomalyDetection/processGroups/{id} |
Authentication
To execute this request, you need an access token with WriteConfig scope.
To learn how to obtain and use it, see Tokens and authentication.
Parameters
| Parameter | Type | Description | In | Required |
|---|---|---|---|---|
| id | string | The Dynatrace entity ID of the required process group. | path | required |
| body | AnomalyDetectionPG | The JSON body of the request. Contains parameters of anomaly detection for a process group. | body | optional |
Request body objects
The AnomalyDetectionPG object
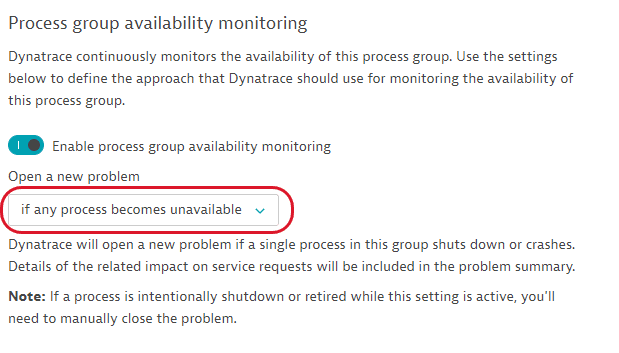
Configuration of anomaly detection for the process group.
| Element | Type | Description | Required |
|---|---|---|---|
| availabilityMonitoring | AvailabilityMonitoringPG | Configuration of the availability monitoring for the process group. | optional |
The AvailabilityMonitoringPG object
Configuration of the availability monitoring for the process group.
| Element | Type | Description | Required |
|---|---|---|---|
| method | string | How to monitor the availability of the process group:
| required |
| minimumThreshold | integer | Alert if the number of active processes in the group is lower than this value. | optional |
Request body JSON model
This is a model of the request body, showing the possible elements. It has to be adjusted for usage in an actual request.
{"availabilityMonitoring": {"method": "MINIMUM_THRESHOLD","minimumThreshold": 5}}
Response
Response codes
| Code | Type | Description |
|---|---|---|
| 204 | - | Success. The configuration has been updated. Response doesn't have a body. |
| 400 | ErrorEnvelope | Failed. The input is invalid. |
Validate payload
We recommend that you validate the payload before submitting it with an actual request. A response code of 204 indicates a valid payload.
The request consumes an application/json payload.
| POST | ManagedDynatrace for Government | https://{your-domain}/e/{your-environment-id}/api/config/v1/anomalyDetection/processGroups/{id}/validator |
| SaaS | https://{your-environment-id}.live.dynatrace.com/api/config/v1/anomalyDetection/processGroups/{id}/validator | |
| Environment ActiveGate | https://{your-activegate-domain}:9999/e/{your-environment-id}/api/config/v1/anomalyDetection/processGroups/{id}/validator |
Authentication
To execute this request, you need an access token with WriteConfig scope.
To learn how to obtain and use it, see Tokens and authentication.
Response
Response codes
| Code | Type | Description |
|---|---|---|
| 204 | - | Validated. The submitted configuration is valid. Response doesn't have a body. |
| 400 | ErrorEnvelope | Failed. The input is invalid. |
Example
In this example, the request updates the configuration of anomaly detection for the process group with the ID of PROCESS_GROUP-52B42D0616D556F5 from the GET request example. It changes the method of detection to PROCESS_IMPACT.
The API token is passed in the Authorization header.
You can download or copy the example request body to try it out on your own. First, be sure to create a backup copy of your current configuration with the GET process group anomaly detection configuration call.
Curl
curl -L -X PUT 'https://mySampleEnv.live.dynatrace.com/api/config/v1/anomalyDetection/processGroups/PROCESS_GROUP-52B42D0616D556F5' \-H 'Authorization: Api-Token dt0c01.abc123.abcdefjhij1234567890' \-H 'Content-Type: application/json' \--data-raw '{"availabilityMonitoring": {"method": "PROCESS_IMPACT"}}'
Request URL
https://mySampleEnv.live.dynatrace.com/api/config/v1/anomalyDetection/processGroups/PROCESS_GROUP-52B42D0616D556F5
Request body
{"availabilityMonitoring": {"method": "PROCESS_IMPACT"}}
Response code
204
Result